HOW TO USE TWO FACTOR AUTHENTICATION IN 2021 WITH EASE
HOW TO USE TWO FACTOR AUTHENTICATION IN 2021 WITH EASE
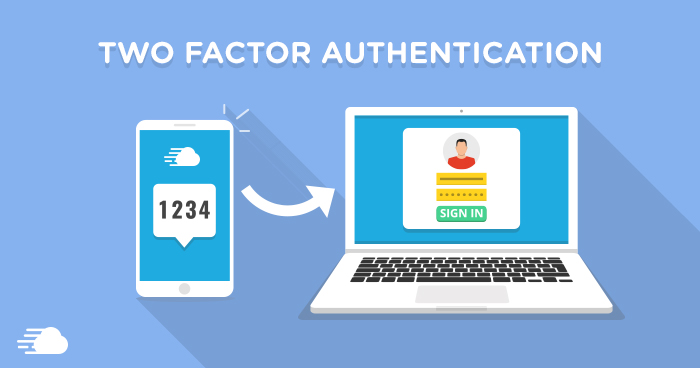
What is Two-Factor Authentication
You might have noticed that some of your online accounts require a PIN number for logging in, in addition to your username and password, and wondered why that is the case. Or you might have pondered why you need to enter your PIN code after you have inserted your credit card into an ATM machine before you can withdraw your money. Such redundant verifications are the applications of an emerging security technique in the world of cybersecurity known as Two Factor Authentication (2FA). The two-step verification process requires that the users enter two pieces of information (i.e., factors) to prove they are who they claim to be thus instituting efficient protection against the rising number of phishing attacks and account takeovers.
Vulnerability of passwords
The concept of passwords has been around since 1960s, and it still is the most fundamental element of cybersecurity today. A password acts like a key to your account by giving you access to what is yours and denying everybody else the same.
Of course, hackers have also been around for just as long as passwords, so back in the days a typical safety guideline to protect your account sounded like "change your passwords frequently", "favor random unique and complex passwords over dictionary words", "use password managers", "set different passwords for different accounts" etc.
However, with burgeoning computing power at the disposal of cybercriminals and a swelling amount of malware enabled by it, passwords alone are no longer sufficient to keep hackers out of your system, no matter how "complex", "random", "unique" or "frequently changed" they might be.
In spite of the fact that passwords are no longer stored in databases in the form of plain text like they once used to (as a safety measure against data breach) and are now stored cryptographically through a process named hashing, a typical 9 character long hashed password can still be cracked by advanced algorithms in just two hours. 2FA acts to increase the number of security layers to the user's login process, thus making it harder for hackers to break in. With a staggering rise in the number of cybersecurity attacks during COVID-19, it is all the more important to add a little more safety to your accounts, and enabling a two-factor authentication system is the right place to start.
Strength of Multi (or Two) Factor Authentication
To truly understand the two-factor authentication system, it is important to understand Multi-Factor Authentication (MFA) first because the former is just a subset of the latter.
MFA basically consists of three fundamental ways (of which there are several derivatives) to gain access to a given entity. These include PIN/password, biometrics (fingerprint, retinal scan or facial recognition), and out-of-band verification methods like SMS. Understandably, 2FA includes any two of the stated verification methods thus affording you significant protection even if your password or network connection is compromised.
Let us now walk you through MFA methods, any combination of which is recognized to be powerful against threats.
PIN / Password
When you sign up for a newsletter or a social media account, you basically create an account for yourself which includes setting up a username and password to erect your first layer of defense.
Push Notifications
Push notifications are gaining popularity as a means of authentication. The most common example is how Google sends authentication codes to previously authorized devices every time a new device associated with a given user requests access. This method provides users with an opportunity to agree or deny the login attempt depending on whether or not they recognize it. If the user provides his/her consent, a signal to the webserver is generated which completes the authentication process.
Out of band verification code
Out of band verification methods rely on connections other than the internet to communicate the code to you. The most common methods are SMS and robocall. Never use email for code verification as that could be easily hacked.
The only downside to SIM-based methods is that if you are traveling abroad and cannot receive your code on your SIM, you are effectively locked out of your own account. Physical 2FA token is emerging as a method of choice which also successfully does away with this limitation. It is a device that works by generating codes to unlock your accounts. For example, Facebook and Amazon both have code generators that work very well with their respective websites by generating unique codes at every login attempt. The downside is, they cannot be used for any other account than the one they are made for.
Biometrics
Biometric verification includes voice recognition, facial recognition, fingerprint, or retinal scan. This method is getting increasingly popular because it is instantaneous. The moment you expose your biometric signature to a computer sensor, it reads your identity and authenticates it thus saving you the time typically spent waiting for an authentication code to be received on your phone.
Authenticator apps
There are numerous authenticator apps on various app stores which work the same way as a physical 2FA token by generating one-time, unique access codes for every login attempt. Both Microsoft and Google have their respective authenticator apps.
Conclusion
In spite of 2FA's effectiveness against ID theft, there is a small price to pay for the additional security you are getting. If you happen to lose your mobile phone, or it just so happens that its battery dies, you will be locked out of all your accounts for which your authentication is set to be via text message, authenticator app, or QR code, and until you recover and resuscitate your phone, you will not be able to get your access back.
However, keeping in view its utility, this price is peanuts particularly in comparison to all the likely losses which can be incurred in the aftermath of cyberattacks which one becomes vulnerable to in the absence of a two-factor authentication system in place. So, the next time you make an account on a website and are asked if you would like to enable Two-Factor Authentication, be sure to click on "Yes".
© 2023 YouMobile Inc. All rights reserved





