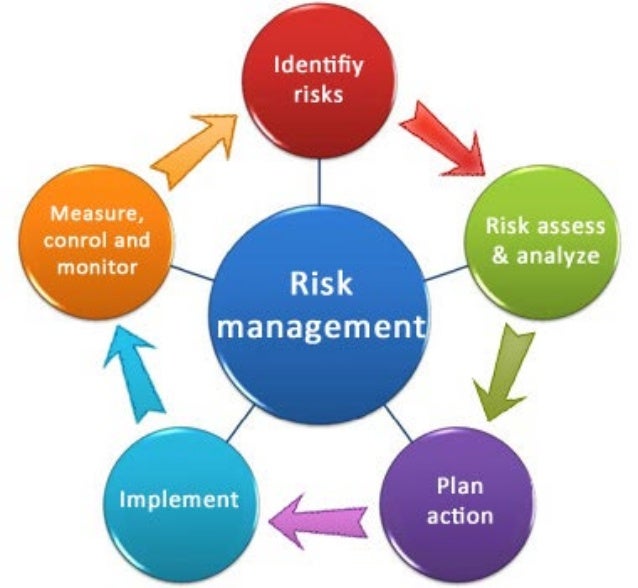
Telecom companies today depend on third-parties to help run their operations. One corporation may have a long list of suppliers on its payroll. Alliances, partnerships, and other relationships can also make part of the business. Granted, they contribute to the success of entities. The only thing that does not work is that they can put the firm at risk for one reason or the other.
Thankfully, extended enterprise risk management (EERM) exists to help reduce the problems that a company can face with third parties. This implies that it is vital even for new business persons looking for telecom business for sale not to start any operations without thinking of implementing an excellent risk management program. There are various reasons EERM is vital for telecom firms and some of them are discussed below.
It Helps Businesses to Have Better Risk Cultures
A business that understands the types of risks it can face from outside forces naturally has better ways of mitigating these tragic events. Ultimately, this can result in reduced volatility giving the establishment a great competitive edge. Preparing well in advance for future risks can help minimize business interruptions, so that everything falls in place as it should.
Enables Investors to Treat Risk as Opportunities
Extended enterprise risk management matters to businesses because it looks at risks in a holistic manner. Businesspersons can view risks in another way as opportunities to go a step further. Investors get to know how to position themselves best to take advantage of market opportunities.
EERM ensures that you are ready for any risks that may come your way. Seeing the risks coming in way before means that you will not blindly walk into a regrettable situation. This ensures that you are always a step ahead in regards to tracking risks that may crop up in the future. As a result, it becomes easier to develop workable strategies making certain your business will not be affected too much on the negative side.
Enhanced Risk Reporting
Another reason it is important for telecom companies to implement extended enterprise risk management strategies is the fact that it helps to support better risk reporting measures. EERM supports more effective reporting, structure, and analysis of third-party risks. This way, a company can have standardized reports that executives and directors can use to come up with improved ways on how to handle these risks. The leadership can identify the areas of business that are more prone to risk. The reports can also help leaders to have a better understanding of risk thresholds, tolerances, and appetite.
Offers Framework for Evaluating Risk
EERM comes in handy when it comes to developing indicators that assist in detecting risk events that can attack an entity in the future. This is beneficial because it makes it possible for the parties involved to offer early warnings. Extended enterprise risk management also offers a more comprehensive viewpoint on different types of risks so that they are handled in the proper way should the risks ever arise.
Better Use of Resources
In an establishment that does not have ERM, you may find that many people have to involve themselves in the process of reporting and managing risks. In most cases, it may not be necessary and a firm may end up wasting resources on this matter. Extended enterprise risk management programs assist a company in regards to enhancing the tools and framework that are used to perform risk management. Note that this does not do away with day to day risk management. It, however, gets rid of redundant processes by making certain that the proper amount of resources are employed to handle risk.

Mobile users are the main driving force behind the growth of internet access across the world. Especially in developing countries, where fewer people have access to personal computers, increasingly affordable data plans and cheap mobile devices allow more and more people gain access to online services. Moreover, rapid growth of mobile connection speeds around the world is a major factor contributing to mobile use. Over two thirds of the global population now have a mobile phone. Mobile devices account for 52% of global internet traffic. The downside of the growing popularity of mobile connectivity is that mobile devices are likely to become increasingly targeted by all sorts of malware. To enhance personal mobile security, 22% of users install VPN on their mobile devices (15% - on their phone, and 7% - on the tablet).
What makes mobile devices a particularly lucrative target?
Portability and size. Mobile devices are so easy to lose. The best that can happen with a lost or stolen mobile phone is it will be wiped clean of all your personal data and sold at a flea market next to a snatched camera and a pair of worn socks. The worst thing that can happen to a stolen phone - if it has no passcode or other locking mechanism - is your personal data will be directly misused or sold separately from the hardware.
Rich personal data. We love smartphones because of their convenience and ability to provide us with technical assets for everyday task management. We collect geotagged photos from our lives (and often task our phone with uploading them directly to the cloud), we install apps to control personal health metrics, to travel (access city bikes, book tickets for domestic and international travel), not to mention gazillions of messages exchanged with our personal and business contacts on a daily basis.
Tons of metadata. Mobile device is something we carry on us almost at all times. It collects, whether we like it or not, vast amounts of metadata about our communications and movements. When you use a Maps app on your phone you allow it to detect your current location in order to calculate an optimal route to your destination, or find suitable cafés and bars in the area.
Personal data you store on your phone, along with ample metadata is what contributes to your digital profile. The place where you start your Google Maps journey most often is probably your home address, and the place where you travel on Christmas day is probably where your family lives. Your connection metadata (what public networks you connect to most often) can reveal a lot about your favourite cafés and bars. Cross-referencing the routes you've taken on public transit with your call metadata (when and who you call) or with your friends' addresses in the contact list can provide an insight into your social activities, identify your closest friends, and patterns of your interaction over a period of time. Not to mention that the articles you read, and videos you watch may reveal a lot about your political and religious affiliations.
Mobile security is a pressing issue both for businesses and for individual users - not least because the two are often connected. Some companies have a strict policy of banning personal mobile devices in the workplace, or connecting personal mobile devices to the office network. It is important to understand that vital component of any cyberattack is social engineering. Two most common ways for your device to be compromised is if you physically lose it, or if you inadvertently open it to ‘hackers' by clicking on a dodgy link in the messenger, or by installing an app whose design leaves a lot of space for exploitation of vulnerabilities.
What is the most common activity for mobile internet users?
Well, social media of course. Facebook still dominates the global social media landscape (over 95% of Facebook users access it on the phone), with YouTube being a close second.
Messaging services are a close second. WhatsApp and Facebook Messenger share and equal amount of global users, followed by Chinese WeChat and QQ (Facebook and WhatsApp are blocked in China).
E-commerce (goods and services) has experienced radical growth in recent years, and it is increasingly adapting to mobile users by creating mobile browser versions of the platform or apps with improved mobile user experience. Mobile purchases are projected to occupy almost 73% of total e-commerce share by 2021 - worldwide, and the growth is particularly steep in the Chinese market. Protecting your financial data is, of course, a number one priority for those who shop online on their mobile phones. But when it comes to online shopping, it is not just your credit card information you need to be careful about. Your purchase habits, your social circles, your shopping schedules are all metadata sought after by advertisers and potential hackers.
7 in 10 apps collect your personal data and share it with third parties, specifically ad services that subsequently bombard you with targeted advertising. Ever wondered why you start getting ads for magical hair loss treatment after you searched an online store for a 'toupee' for your Halloween costume? Even more creepy is data harvesting designed into phone and tablet apps for children - logging location and network metadata of each user.
Despite the evolving privacy laws in some jurisdictions (like the General Data Protection Regulation in the EU), protecting the mobile device and personal data you store on it is each individual's responsibility. Encrypting your mobile data, being careful about the apps you install on the smartphone, avoiding public WiFi - and using VPN when you have to connect to it - these are just the minimum of measures one can take to ensure personal mobile security.
More information about VPNs and how can they improve your mobile security: https://vpnpro.com/

Whether you are trying to pay a bill, order something online or just trying your luck at an internet casino, safety of the payment system is of paramount importance. A single mistake can result in phishers and scammers stealing your financial details, which could prove to be very costly. So, how do you make sure that your financials are safe while spending money online? By sticking with reliable websites and trusted payment systems. How do you make sure they are safe options? That's exactly what we are going to discuss next with the help of the following points.
Safety Begins at Home
The computer you are using to surf the internet is the first thing that you need to secure. Make sure that the OS running on it is original first because that's the most important aspect of cyber safety. Next, you need to install a good antivirus software with real-time internet protection. This will give you continuous protection even if you are led towards a phishing page or a site that's deemed unsafe. The antivirus will detect and stop suspicious activities automatically and warn you of the danger immediately.
Use e-Wallets
The main advantage that electronic wallets have over using credit cards and debit cards directly is the fact that they keep your card information safe. For example, internet casinos are a hotspot for cyber criminals, so they are always looking to phish card info from unsuspecting users and that's precisely why online casino PayPal payment option is the safest choice to make. PayPal being one of the world's most popular and also one of the most reliable online payments system, your financial info remains safe with them and you don't ever have to risk giving away your valuable financial information on a scam site or phishing page. The best part is that almost everyone accepts PayPal these days!
Do Your Research
If you are going to play at an unknown internet casino or shop at an ecommerce site that you know little of, use Google. See what other people are saying about the site and go through user experiences to get an idea of what to expect. Some sites even have a trust score for users to check.
Check the Link/URL
The best and often the only way to avoid an active phishing attack is to check the URL in your browser or mail. For example, does it say https://amazon.com or does it say https://amazon.us/gb5hgy/login-id? Most authentic websites do not use a string of random alphabets at the end like that and Amazon USA is just called Amazon.com, so there's no amazon.us domain. Beware of little details like that at all times.
The rule of thumb is, if something looks out of place, then that's because it is! Don't take chances with your finances online and be safe by following the few simple precautions mentioned here.

With the majority of us owning a smartphone or tablet keeping our identity safe is vital if we are going to carry on sourcing and buying goods and services online.
Nothing is more frustrating than falling foul to a scam, and although the total amount of fraudulent conduct which was reported in 2017 dropped by 6 percent, the percentage of identity fraud is up, rising by 1 percent in 2017 to a total of 174, 523 cases.
Identity fraud remains a problem mainly by those using the internet, with 84 percent of that identity fraud taking place through online application channels.
It's no wonder then that people are becoming increasingly worried about using their smartphones to have a bet or wager online as many sites require your personal and banking details in order for you to become a member.
On a positive note, the majority of gambling sites are highly regulated and have strict rules to stick to making them a pretty safe bet to play at, but if those rules and regulations still do not convince you then maybe being able to play and pay for your games without having to divulge your banking details will appeal.
If you do enjoy using your smartphone for gaming when you have a few spare minutes in your day then perhaps using a mobile casino pay with phone credit is the way to go for you? Using this method means that there is absolutely no need to give the site any banking derails, in fact there is no need to have a conventional bank account at all.
The way this payment option works is by either using your pay-as-you-go account taking off the cost of your games from that or adding the cost of your games to your monthly contract. Boku makes it possible to play your games without having to give any banking details to any site that accepts this payment option which will, for many, make their time online more enjoyable.
We all lead busy lives and over the last decade or so we have come to rely on our smartphones to complete tasks that would have eaten time out of our days, the thought that we could have our online identity stolen and even worse then used for some criminal activity worries many of us so taking steps to stay as safe as possible whilst surfing the net is paramount.

With all the developments in mobile devices these days, it is easy to let some things slip you by. For users making their way from beginner to intermediate user and beyond, there might be some components of mobile devices with which you are not familiar. Here we'll go over some basic information on VPNs to help you understand what they are and how they are used - and with this, you might get some indication on whether or not they're right for you.
The Basic
VPN stands for Virtual Private Network, and in simple terms can be thought of as a go-between between your computer and the internet at large. When connected to a VPN you receive your data from the VPN, and the VPN service itself is responsible for sending and receiving your internet data requests. The benefits of this come primarily down to security, geo spoofing and evading various limitations imposed by your connection point.
When you have a VPN, any attacks have to come through the VPN service, rather than directly to your computer. As VPNs (especially professional ones) have improved security over most basic computer setups, they manage to take a lot of slack for the end user. There is also the added complexity in attacking through a VPN, which again benefits the end user.

"Internet Security Padlock for VPN & Onli" (CC BY 2.0) by mikemacmarketing
Geo-spoofing is a term applied to tricking a website or server into thinking you are from a different location. Sometimes websites or videos are locked behind geographical requirements, so this can be an easy an effective method of circumvention. The same can be said for limitations placed by the connection point themselves. Commonly, this can be seen in free Wi-Fi places like public transport. While the blocking of certain websites is a good idea, they can be overzealous, blocking places which are safe and offer no significant bandwidth drain.
The Modern VPN
Modern VPNs are far from the sluggish old behemoths we had to deal with a decade ago. These days, VPNs can not only access largely the exact same web pages and services as natural connections, they also can do so at a speed which renders them similar in performance.
These days there are an enormous amount of VPNs to choose from, thanks to improving technology and a great market demand. If security is a big concern for you, as it should be, then check out our other articles. These can help to help to decide whether the rest of the features are a good fit for you.
Once you have decided on a VPN service ExpressVPN, we recommend checking out some of the many online reviews, which can help you narrow down the pros and cons, and get the most out of what is right for your devices. Remember to be thorough and read closely, some of them might come with features you didn't even know you would like.
The Take Home
VPNs are becoming more common for a reason. With issues like Net Neutrality raising to the forefront of social conscience our privacy, safety, and freedom of choice and speed have never faced so many threats. The right VPN can help protect you not only now but can help ensure that in the future you are inoculated against many of the issues that governments or businesses see fit to throw at you. Just be sure to use your powers for good.

© 2023 YouMobile Inc. All rights reserved





