
Mobile phone tops the list of the most used gadgets by us every day. Right from the mail which can close a million-dollar deal to making the long distant video call, we rely on mobile phones very much. It can turn out very bad if these devices are left unprotected. There are various security apps other than antivirus apps which can help us to keep our mobile phones and the data stored in it to be safe and secure.
Some of the top security apps for Android phones are listed below:
Applock

This app is life-saver for many people. It works like the vault in banks. You can keep your photos and videos locked under it. Also, users can lock other apps such as Gmail, mobile and online casino gaming apps, internet banking apps and so on using Applock. You can use a secret PIN to access the files and apps. By this way, your mobile phone will have two layers of security. This app is available in the Google Play Store for free.
DuckDuckGo Search and Stories

In the world of internet where major conglomerates make use of the personal data of people, DuckDuckGo is a gem. This is a search engine like Google and Bing, but it does not track what you search online. If you are concerned about private companies accessing the information you surf on the internet, then DuckDuckGo is the perfect solution.
Find My Device by Google

Find My Device was earlier named as Android Device Manager. This app will help you to find your mobile phone. It can show you the location of the phone and you can also make the phone ring using this app. You can also remotely lock and erase the information stored on the phone. It does not have any ads and in-app purchases which makes it clutter free.
Firefox Focus

Firefox Focus is one of the most secure browsers out there. The app can be used to remove the advertisements and trackers to some extent ensuring more private browsing. The best part is that this app is also free.
Glass Wire

Glass Wire is one of the new best apps to track the data consumption effectively. It has the options for the players to see the data usage in terms of days, weeks, months and by individual apps. This can help the users to find any irregular activity of the apps in the background.
Resilio Sync

Resilio Sync will help you to create a safe cloud storage of your own. You can turn your PC or desktop into a cloud storage. In simple terms, it is like Google Drive. It can help the users in keeping the data under their control rather than trusting private companies.
LastPass
LastPass helps the users to save multiple sensitive passwords and restore it to the respective sites. All the passwords will be locked with a master password. This really helps if you visit a lot of sites or handle multiple accounts.

Jackpot Fruity has come up with the list of the above-mentioned non-antivirus apps which provide top security for all Android phones. Since the rate of cybercrime is increasing, security in mobile phones should be taken seriously as they contain sensitive data.

When it comes to our mobile devices we tend to take security for granted. In truth, these devices are open to the dangers of the Internet just like a computer is. This is why you should consider using a VPN when using your device on the Internet.
So, what is a VPN? A Virtual Private Network is a buffer between your connection and the rest of the Internet. When using a VPN, you are able to hide your IP address and use the Internet not only anonymously but also spoofing your location, so as not to give your geolocation away. It also allows you more security on your device too.
Now that we know what a VPN is, this is why you should use one on your mobile device:
Privacy
With your mobile device chances are you are going through many public areas and using their hotspot Internet access. Each time you do this you can be opening up your data to possible hijacking. If you use this device for work, that means that sensitive data could be passed around too. What a VPN does is to protect your connection and your data from outside interception. The fact that your data will be encrypted too also gives that added level of protection that you need.
Connectivity
A mobile VPN can act like a permanent connection to your home or work server. This is beneficial if you enjoy gaming on-the-go. The best Android VPN's connect to your Internet connection, and use that to create a more stable Internet access for your phone. This is always a plus, especially when your online activity requires that reliability.
Spoofing your Location
Through using a VPN in a different area of the world not only do you open up geolocked content, but you also can find that foreign websites open faster. If you visit plenty of foreign sites on your phone, or want to connect to faster game servers around the world then this can prove invaluable.
Flexibility of the VPN
Through the way, you connect to a VPN through your Internet connection rather than through an App, this leads to flexibility in the type of connection you can use. This includes wi-fi, 4G networks and any other connections available to you. It all works on the same protocol.
VPN isn't Used for Phone Calls
Unless you are using a service like Skype, be aware that VPN does not encrypt your phone calls. This is something that you should be aware of when using a VPN service. If you want your calls to go through VPN then be sure to use a IP voice service.
The main reason to use a VPN on your phone is of course security. In this day and age with hacking and cyber-crime seemingly rising in prominence, we have to be aware of the dangers towards our personal data. VPNs are the best way to protect yourself, along with virus scanners and malware checkers of course. Always be aware of the dangers that are out there, and take action against them, so that you can concentrate on the more important task of your mobile device (to have fun).

Source: Kai Oberhäuser on Pexels.
DDoS or Distributed Denial of Service attacks are the great bogeyman of the internet - vague and mysterious to many, and all the more threatening for it - but the idea is relatively straightforward when compared to lesser known concerns like cross-site scripting; DDoS attacks launch data at a web service or server until it breaks.
Attack Surface
As far as the tools of cybercrime go, DDoS attacks have been around for a long time but it's debatable when they first became a part of the public consciousness. Last year, a DDoS attack involving the Mirai "botnet" -- a horde of zombie devices twisted to the whims of a criminal -- took down half the internet by overwhelming the company responsible for turning domain names into IP addresses - Dyn. Early attacks go back to 1995 though, when an Italian activist group used the technique to protest nuclear policy in France.
So, with online criminals recruiting everything they can get their virtual paws on into botnets, including "smart" security cameras and baby monitors, why isn't the world living in terror of an Android or iOS-based DDoS attack? With around 2.32 billion devices on the market, the attack "surface" (i.e. the size of the space that attackers can exploit) presented by smartphones is enormous but the only major example of what could be deemed a DDoS attack on mobile was, ironically, done by users themselves way back in 2004.
Happy New Year
According to UK website The Register, a glut of "Happy New Year" texts and phone calls sent on the last day of 2004 added significant pressure to mobile phone networks throughout the country, slowing delivery to a crawl. It has to be the most mundane, accidental denial of service attack in history but it's nevertheless indicative of the kind of situation people were scared of just after the turn of the millennium. Experts at the University of Pennsylvania State suggested that "SMS-overload" could disable communications even in huge cities like Washington.
Security is a major concern for any businesses with an online presence and many install web application security solutions and DDoS mitigation to mitigate the threat. For instance, web application firewalls - cloud-based security barriers that stand between malicious traffic and delicate systems - protect against SQL injections, cross-site scripting, and other distinctly modern ills. Botnet protection keeps your router or webcam from launching a DDoS attack.

Source: JÉSHOOTS on Pexels.
Trojan
Recruiting a phone into a botnet usually requires the owner to download a fake app - a trojan, a type of malware that pretends to be something harmless to trick users into installing it - to give a criminal access. For example, a DDoS Trojan called Android.DDoS.1.origin imitates the Google Play Store but, behind the scenes, it works with a handler to send text message spam or join a larger botnet.
As both Google and Apple vet their apps before adding them to their respective stores, fake software, malware, ransomware, and a range of other concerns usually come from unofficial third-party providers. With that in mind, malware is almost the exclusive domain of the more experimental mobile phone users or people who download pirated apps. So, while it has been true that almost all mobile malware is on Android, only a fraction (0.1%) came from the Play Store; the rest is hidden out in the wilds of mobiledom.
Finally, most internet activity on mobile phones is undertaken in apps. As apps use dedicated connections (Pokémon Go only connects to Niantic while the BBC app only talks to the BBC's servers, for example) they can be more secure than a mobile browser, simply because Chrome and Internet Explorer encounter more potential threats from ad networks and dodgy links. Mobile is more of an exclusive club or "walled garden" than desktop, presenting far fewer opportunities for criminals to take advantage of.
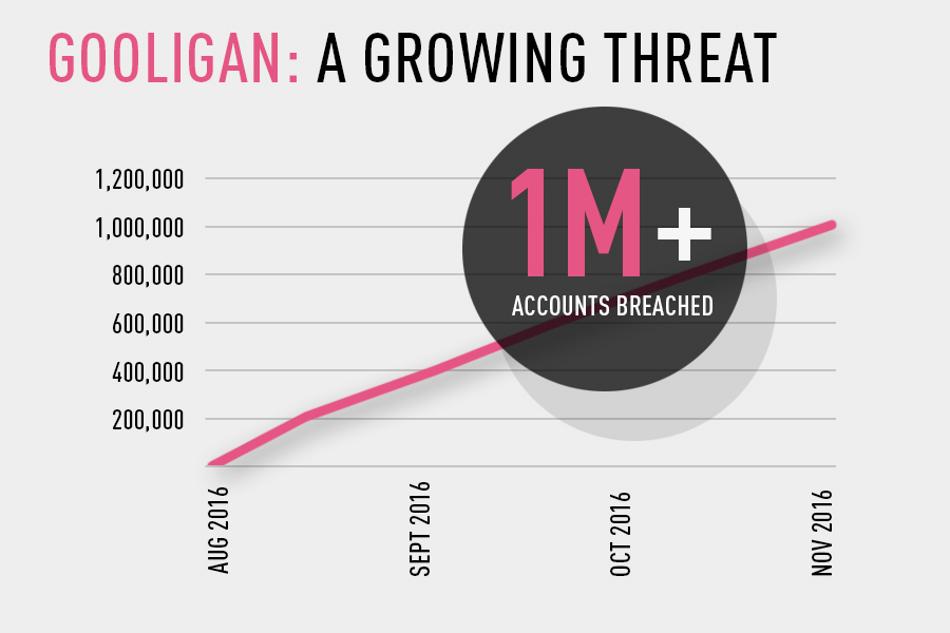
Gooligan is a malware that hides within Android applications found mainly outside the Play Store, but it has recently been found that multiple apps available on the Play Store are also infected by it. The malware utilizes two vulnerabilities (Vroot and Towelroot) prevalent in pre-Marshmallow Android builds to root devices and gain access to email information, as well as authentication tokens, including those of your Google account. Gooligan then uses this unauthorized access to install applications from the Play Store itself. This of course, is done to increase the revenue associated with in-app ads. Additionally, the afflicted accounts are made to leave a 5-star review for the concerned app, without the user even being aware of what's going on.
If your device is running on Android Lollipop or an even lower version of the Android OS, Gooligan can affect your device. The secret malware was found by a cyber security firm called Check Point and they have since reported that Gooligan can access Gmail, Google Photos, Google Docs, G Suite, Google Play and Google Drive on all the 1 million plus devices that it affects right now. In response to the report, Adrian Ludwig, head of Android Securities, has explained that so far, the malware, which is a variant of the previously discovered Ghost Push, has not shown any intent to steal information and has instead been only associated with promoting in-app revenue through falsified reviews and unauthorized app installations. Google has since revoked all affected tokens and has banned multiple affected apps from the Play Store.
In the words of Check Point, "Gooligan potentially affects devices on Android 4 Jelly Bean and KitKat, and 5 Lollipop, which is over 74 percent of in-market devices today. About 57 percent of these devices are located in Asia and about nine percent are in Europe,"
In order to check and see if you are affected by Gooligan, enter your email address and see for yourself at: https://gooligan.checkpoint.com/
Head over to https://forum.youmobile.org/downloads/ to find all the latest updates for your smartphone.
Saikat Kar (tech-enthusiast)
© 2023 YouMobile Inc. All rights reserved






