
The Apple Vision Pro recently won a prestigious award for its operating system: visionOS. UK's Design and Art Direction Awards (D&AD) gave visionOS the Black Pencil. Apple CEO Tim Cook took to X to congratulate the design team and praise Vision Pro's profoundness.
The Black Pencil is D&AD's most coveted accolade. visionOS is the first Apple product to win a Black Pencil since the iPad in 2011. And it is the first Black Pencil awarded to Apple while Tim Cook is CEO. Understandably, Cook is quite pleased.
In addition to congratulating the Apple design team, Cook said Vision Pro was made possible by "years of breakthroughs". He also revealed he has seen people become emotional when they first try a Vision Pro.
I can understand that. The Vision Pro is one of the best AR headsets the XR industry has ever seen. Its micro-OLED displays are fantastic and its hand and eye tracking is not only accurate, it's also brilliantly implemented. You simply look at what you want to open and then do a pinching gesture.
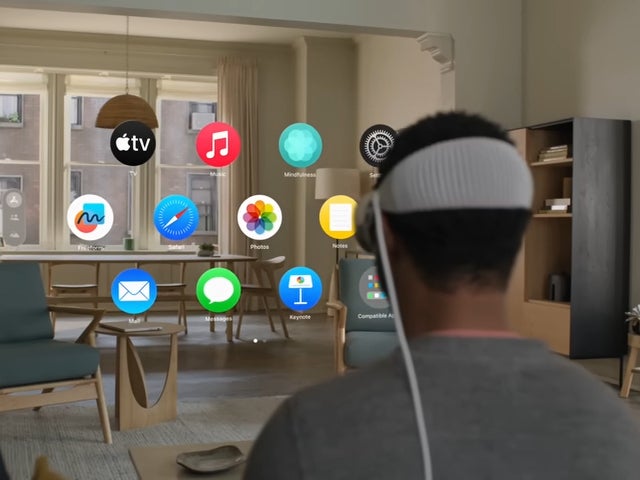
But I think there might be another reason as to why people are getting emotional when using a Vision Pro. It might be the first time they've ever used a VR device in their life. The Vision Pro is excellent but the much more affordable Meta Quest 3 is no slouch either.
If you took someone who had never used VR headsets before and made them play Microsoft Flight Simulator 2020 on a Quest 3 they'd be pretty emotional too. What the Apple Vision Pro does however is provide users with a very intuitive user interface. And Apple being a big name makes people want to try its headset, even if the same people might have brushed off VR as a fad before.
Only 25% of U.S. adults have used VR in their lives. Those who haven't show little interest in it. But 80% of people who have used VR keep coming back for more. So even before the Apple Vision Pro people were clearly being wowed by VR and retention was high. Apple's foray into the XR industry is simply bringing more eyes to XR in general. Something I am quite pleased about.
However, until a cheaper Vision Pro 2 comes out, Apple's headset is going to remain out of reach for most consumers and enthusiasts. Also, I personally think the Vision Pro should get dedicated controllers and official support for PC VR games and other VR games as well. That would truly make Apple's XR devices worth the premium in my opinion.

Should You Outsource AI Development: Pros and Cons
According to a recent study, 94% of tech firms rely on external providers when it comes to advancing their AI technology. Outsourcing has become a trend during the pandemic and doesn't show signs of stopping nowadays. This blog post sheds light on the pros and cons that outsourcing of artificial intelligence development carries for your tech company. So, whether you doubt whether external providers are the right choice to power your IT initiatives, this is your answer.
Pros of AI Development Outsourcing for Tech Companies
Sometimes, the best way to power your tech company is to look outside your organization, and outsourcing comes as a strategic move here. Let's take a look at the most sufficient advantages that they reap from outsourcing AI development.
Access to Vast Talent Pool
AI development outsourcing allows you to tap into skilled and experienced artificial intelligence developers regardless of their location. Unlike in-house hiring, you don't have to spend time and costs on filling the workforce shortages with talent from your location or searching for candidates willing to relocate. Outsourcing allows you to have the right expertise on board, bypassing geographical limitations and thus boosting the time-to-market speed.
Cost Savings
Apart from the variety of skilled workforce, AI development outsourcing helps to cut down on expenses related to hiring and training in-house teams. First, the outsourced team has all the required infrastructure and equipment for AI development. Second, outsourced teams allow tech companies to save on insurance, health care, travel, and other employee perks. Third, outsourcing allows for cutting down on budget by hiring contractors from countries with lower labor costs compared to Western world. Apparently, outsourcing AI app development allow tech companies to benefit from cost effective solutions without compromising on the quality of the final product.
Scalability Options
Just like any project, AI development can get unpredictable from time to time, and outsourcing has the "built-in" flexibility to address the changes. Depending on the project requirements, you can "fill the gap" in the development team with a lacking talent or scale down on the workforce that you don't require at the particular stage with no commitments involved.
Cons of Outsourcing of AI Development
Before outsourcing your AI initiatives, let's consider the most significant risks associated with trusting AI development to third-party contractors.
Data Security and Confidentiality Concerns
Sharing sensitive information with external providers may pose serious threats to the security of your organization. This may be a sad consequence of unreliable data protection measures and negligence of third-party contractors as well. Make sure the service provider is trustworthy and implements robust data protection measures in place.
Communication Challenges
These may be either cultural, language, or time zone barriers. Since effective communication is a key to project success, make sure to hire the team that not only speaks the language required but also understands your values and standards.
To sum up, many tech companies rely on external providers to advance and implement their AI initiatives. No weird, considering the cost savings, flexibility, and a vast talent pool that outsourcing grants. If you're a tech firm looking to reap the benefits of AI development outsourcing, S-Pro comes in as your reliable development partner. Their dedicated team of AI specialists uses cutting-edge algorithms and machine learning techniques to craft intelligent solutions that deliver tangible results to your tech company.
There is an opinion among marketers that those SMM principles that provide good results in European countries are not as effective or even ineffective in the United States. In this regard, several myths about promotion on American social networks were born. And since they remain popular for a long time, this indicates that many people believe in them.

Let's examine the most common of these myths now and immediately provide reliable information on how SMM works in Utah.
We'll look at these top myths that were successfully broken by a Digital Marketing Agency:
- Social media is only for the young;
- Targeting doesn't work in the US;
- Amazon doesn't work with SMM.
We are sure that this information will be useful when drawing up a strategy for promoting your business on popular social platforms.
Myth 1: Social Networks Are Only Popular Among Young People
According to anecdotal evidence, the main audience of social platforms is people aged 18 to 25. Allegedly, with age, interest in business on social networks disappears, and Americans prefer sales at Walmart, Best Buy Co., etc.
The myth, most likely, was born among fans of American TV series and those who firmly believe that cinema reflects the real way of life in the USA. According to the scripts of many films, American adults spend their weekends at sales or in the evenings watching TV programs in the "shopping on the sofa" format.
However, in the United States, the main buyers on social networks are the 18 to 64-year-old population. Moreover, the older audience no less actively orders goods on popular platforms, preferring passive shopping to trips to hypermarkets.
Myth 2: SMM Is Ineffective When Promoting on Amazon
The bottom line is that promotion on social networks will not bring the desired result for such a global market giant. It is better to promote your business on Amazon through other techniques.
Where the myth came from: it's hard to say. Rather, its appearance was influenced by the belief that only young people use social networks, i.e., this is a less solvent audience with a certain range of interests determined by age.
Nevertheless, we remember that in the United States, people of different ages are on social networks, including retirees. This means SMM will be useful for Amazon, just like other platforms or sites.
Promotion on social networks helps build a community, and people will be interested in products and provide feedback through reviews.
Myth 3: Target in the USA Is Ineffective
In the USA, social networks receive a lot of advertising, which is why they have become boring and the public needs to react more to them.
The myth was invented by someone who did not know how to analyze the target audience and set the target settings. The unfortunate marketers who stepped on the same rake or those who did not even try to set up advertising on social networks in the States picked up this fiction and released it to the masses.
If you analyze your target audience and fine-tune your targeting, you can find buyers even in a very specific business niche.
Conclusion
Now, you've found out some basic myths about social media marketing in Utah and other parts of the USA. Let's take away that SMM is appropriate for both young and old people.
It is highly effective on platforms like Amazon and, when used with proper targeting. This means that SMM has to be well-known and applied as a promotional tool that has a good effect in the saturated U.S. market.

In the fast-paced world of college life, your mobile phone becomes more than just a device; it's your lifeline to the world. Your phone does everything from staying on top of class schedules to keeping in touch with friends and family. But with the right accessories, you can elevate your mobile experience to new heights, making your college life easier and more enjoyable. Here are ten must-have mobile accessories that every college student should consider.
1. Portable Charger
Let's face it: a dead phone can mean missing out on important updates or being unable to navigate your way around a new part of town. Similarly, a heavy academic workload can overwhelm you, making it tough to manage your studies efficiently. At such times, you may wonder, "Who can do my coursework?". If so, finding an essay writing service that offers academic aid can be just as much a lifesaver as a portable charger or power bank for those long days on campus when you're away from a power outlet. With a range of services tailored to meet your academic needs, you can find the support necessary to keep your grades up while managing your busy college life. It's like having an academic energy drink for your studies, always there when you need a boost.
2. Durable Phone Case
A durable phone case is the knight in shining armor for your mobile device. Whether it slips out of your hand as you rush to class or gets crammed in your bag with textbooks, a robust case can save you from the heartache (and expense) of a cracked screen or worse. Plus, with endless design options, your phone case can also be a form of self-expression, showcasing your style.
3. Wireless Earbuds
Wireless earbuds are a game-changer whether you're tuning into an online lecture, listening to your favorite tunes, or catching up on podcasts during your commute. They free you from the tangle of cords and make it easy to switch between devices. Look for a pair with good sound quality, a comfortable fit, and a case that doubles as a charger for added convenience.
4. Screen Protector
A screen protector might seem minor, but it's like an insurance for your phone's display. It protects against scratches, smudges, and even the impact of drops, ensuring your screen remains as good as new.
There are various types of screen protectors:
- Tempered Glass: Offers robust protection against scratches and impacts, mimicking the feel of the original screen.
- Polyethylene Terephthalate (PET): A plastic-based option that provides basic scratch resistance and is budget-friendly.
- Thermoplastic Polyurethane (TPU): A flexible option that self-heals minor scratches, offering a balance between PET and tempered glass.
- Anti-glare: Reduces reflections and glare from sunlight or bright light, ideal for outdoor use.
5. Multiport USB Charger
With the many devices a student needs to keep charged, a multiport USB charger is essential. It allows you to charge your phone, tablet, earbuds, and other devices simultaneously, saving you from the hassle of juggling multiple chargers or fighting over limited outlets in your dorm room. It's the ultimate charging station for the tech-savvy student.
6. Phone Stand
A phone stand might not seem essential until you've tried using one. It's perfect for hands-free video calls, watching lectures or tutorials, or simply keeping your phone in view and accessible on your desk. Some stands even come with features like wireless charging, making them a multifunctional addition to your study space.
7. Bluetooth Speaker
A portable Bluetooth speaker brings the party wherever you go, from impromptu gatherings in your dorm to chill study sessions in the park. Look for a great sound quality, a durable design, and a long battery life. It's a great way to enjoy music with friends or add a soundtrack to your solo adventures.
8. External Hard Drive or Flash Drive
While not directly a mobile accessory, an external hard drive or flash drive that connects to your phone can be incredibly useful for backing up important documents, photos, and videos. It's a secure way to ensure you never lose your essential data, even if your phone meets an untimely demise. Plus, it makes transferring files between devices a breeze.
9. Smartwatch
A smartwatch keeps you connected without always having to pull out your phone. It can notify you of important texts, emails, and calls, track your fitness activity, and even help you manage your calendar. For busy college students trying to balance school, work, and social life, a smartwatch can be a convenient way to stay on top of it all.
10. Camera Lens Attachments
For aspiring photographers or social media enthusiasts, camera lens attachments can transform your phone's camera into a more versatile tool. With options like wide-angle, macro, and fisheye lenses, you can experiment with different photography styles and elevate your photo game without needing a bulky DSLR.
In Conclusion
Armed with these ten mobile accessories, you'll be ready to tackle college life head-on. Not only do they offer convenience and efficiency, but they also allow you to have more fun along the way. So, gear up and make the most of your college experience, both online and offline.
Author: Sam Stahl
Sam Stahl is a seasoned article writer and tech expert with a knack for breaking down complex technological concepts into easily digestible content. His extensive knowledge spans the latest gadgets, software, and cybersecurity, making him a go-to source for tech enthusiasts and novices. Through his engaging articles, Sam aims to empower readers with the information they need to navigate the ever-evolving tech landscape.

Developing a mobile app takes significant time, effort, and investment. But once the app is ready for launch, the real work begins. Without an effective marketing strategy, even the most ingenious app will fail to attract an audience.
This article will cover some of the core marketing strategies that can help a new app thrive.
Creating an App is Only the First Step
Without an excellent post-launch marketing campaign, even the most innovative and useful app can still be in danger of languishing in oblivion. The most efficient way to obtain such a strategy and successfully put it into practice is by hiring a professional team with an excellent reputation. By visiting Radaso.com, you will find one of the most reliable mobile app marketing agencies that offers a performance-based pricing model.
Robust post-launch marketing is a must-have for any app developer seeking success. This involves tailored branding, targeted advertising, strategic partnerships, and more.
When done right, marketing not only boosts app visibility and downloads but also drives revenue growth and long-term sustainability.
Utilize Cross-Channel Digital Marketing
As a strong start, run your marketing campaigns across key digital channels, targeting your ideal users based on demographics and interests. For example:
- Facebook and Instagram ads can deliver your app to specific audiences at scale.
- Strategically placed ads on YouTube and TikTok also effectively raise awareness among the highly engaged users of these platforms.
To maximize visibility, app store optimization should be a priority as well, involving keyword research, compelling descriptions, and imagery, plus monitoring user reviews.
Email marketing to existing users or mailing lists, guest blog posts, social media organic content, and PR outreach to journalists and influencers should round out the cross-channel approach.
Build Strategic Business Partnerships
Another powerful marketing avenue is forging win-win partnerships with relevant businesses and influencers if your app caters to a particular niche or industry. Seek out brands in that space to co-market the app to their customer base through email, social media, and website integration.
Influencer marketing should be part of the strategy too. Research micro-influencers and industry experts who align with your brand and can promote your app to their engaged follower base.
Optimize the Post-Download Experience
Marketing cannot stop once users download the app. Ongoing optimization is key to user retention and conversions. Employ push notifications judiciously to highlight new features or timely content.
Send seasonal promos and special offers custom-tailored for specific user groups. Monitor feedback and continually improve navigation and user experience. The app must address real needs and pain points. This drives organic social sharing that money can't buy.
Measure and Iterate
Continually assess marketing performance through key metrics like cost per install, retention rates, lifetime value per user, and ROI. Identify winning strategies and double down on them. Eliminate underperforming initiatives and test new approaches.
Conclusion
Always follow modern frameworks for promoting your app among users. Outdated methods can only harm your reputation and may not work as needed. If you're unsure how to do it right, seek help from professionals.
© 2023 YouMobile Inc. All rights reserved





