
Android have proven itself to be the ultimate adversary to the mighty Apple as far as smartphones, tablets and even laptops are concerned. However, the plucky Android systems are much more susceptible to viruses and hacking than their Apple based rivals - how can you boost the security of your Android device to the maximum?
Downloads
Firstly, only download applications from the Google Play Store. It sounds obvious but Android won over a lot of fans thanks to their infinitely customisable offerings and the nasties of the internet are all too aware that you can't get the ultimate custom through the Play Store. In the settings tab of your Android device; head to security and un-check the unknown sources box to block downloads from unreliable/potentially harmful sources.
Permissions
Even the apps you download from the Play Store have the potential to compromise your device if you aren't vigilant when installing them. If a game you've installed asks for access to your SMS or internet history then there's every chance something about it isn't right. You can refuse certain permissions for apps and you can even disable potential security risk apps through settings > enabled apps.
Passwords
The stronger the password, the less likely it is to be hacked. Always avoid birthdays, your own name and former addresses because this kind of information can all be drawn from your Facebook page.
Data Encryption
Essentially, if you encrypt the data on your phone or tablet then no-one you don't want to access it will be able to. The encryption relies on a strong password, of course, so make sure it's a secure one just in case.
Wi-Fi
If you want to play on platforms like southafricancasinosites online casino using public Wi-Fi, maken sure it has a security password, don't join it unless you're 100% certain it's safe. BT, O2 and various other providers do offer Wi-Fi access without any security procedure and even they ought to be treated with caution - you never know who might be providing the connection and what they can do with it.
VPN
Without doubt, the best way to access the internet securely is VPN. Virtual Private Networks are like protected wormholes to the internet as nothing can get in to access your data - nothing you don't want of course. VPN access isn't expensive and the vast majority of modern routers have VPN capability built into them making VPN access free to you. Ensure you do your research and check out sites that review the best VPN for Android devices. Once you;ve found one, make sure you set VPN as always on for your Android device should you have access; if you haven't get access ASAP.
Disable Notifications
Notifications from apps and platforms like meilleurs casinos en ligne français, they can also be viewed over your shoulder by someone you don't want to see them. Mobile banking, as an example, may send you a notification to confirm a deposit has cleared - do you want the world knowing that? No, you don't!
Remove Unnecessary Apps
If you haven't used a particular app in a long time, it may be best to get rid of it altogether. The more apps you have, the more likely it is that one of them will be compromised and causing harm to your Android device. Many apps collect data in the background that is then forwarded to the creators for purposes we just don't know about - delete them before they cause irreparable damage.
BitRaser File Erasure is a privacy protection software that enduringly deletions folders, app traces, Internet browsing history, sensitive files, saved login passwords, etc. desktop and server, stored on laptop beyond the possibility of data retrieval. Meanwhile, this software meets everyday media decontamination needs of organizations and entities via protected erasure of data. On the other hand, it highly enables you to schedule file erasure and keep up comprehensive log reports of all deleted files.
Outstanding capabilities of BitRaser File Erasure software
There are a lot of amazing capabilities widely involved in Bitraser file erasure software. Let's take a deep dive to discuss the excellent capabilities comprised of file erasure software. They are:
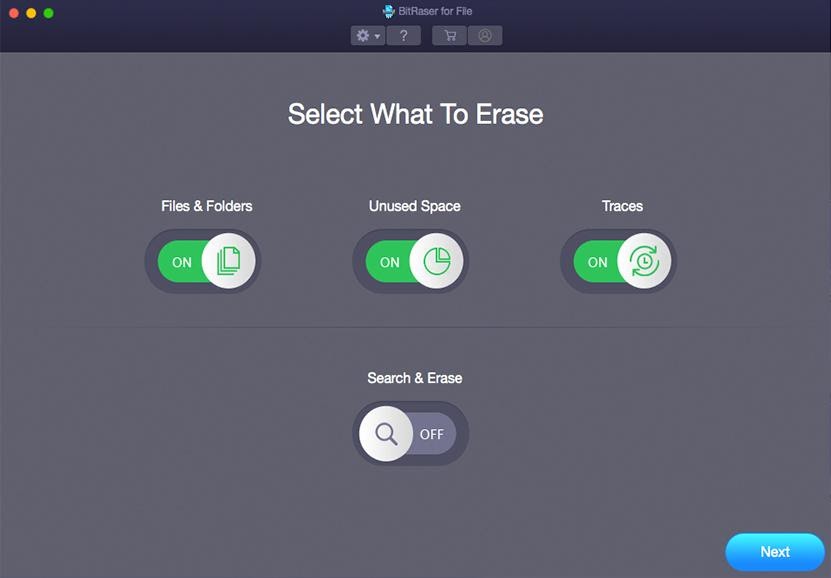
Protected file and folder removal
Safely deletion sensitive files from Mac, Laptop, Desktop, and server beyond retrieval, thus guarding data secrecy.
Great-speed erasure
It performs great-speed and instantaneous deletion of various files with the choice to pre-schedule file deletion jobs.
Email and Browser history erasure
It smears emails and browser history, and records are residing in any media, drive, or server with no send-off any traces.
Erases partitions
Securely deletion logical drives or partitions with no hurting applications and OS (Operating System) files.
Eliminates browser history, cookies, and application traces
It erasure browser history and cookies alongside with utmost lately utilized application traces that follow your habit pattern.
Certified deletion
Makes certificate of deletion to aid meet constitutional and governing compliance.
Technical specification of BitRaser File Erasure software
In this part, some of the technical specifications mentioned below that are broadly involved in BitRaser File Erasure software. Just pay your full attention and know the technical specifications of the file erasure software.
Certified File Erasure
- It permanently deletes one or many files beyond recovery.
- Erasures files, folders, and partitions.
- It greatly erasures system use and browser history.
- Erasures application traces.
- Erasures not used space.
- Remotely erases folders and files on storage and server zones throughout the network.
- Supports seventeen global erase standards.
- It erasures files from charted drives in your system.
Configuration and Automation
- Option to calendar erases jobs at periodic intervals.
- Calendar erase of chosen files on the workplace and servers on the regional zone network.
- Option to hunt for a particular file utilizing its term.
- Capability to make erases catalog comprising the terms of folders and files that can be easily removed in one step.
- Prevent unauthorized erases via password protection.
- Option to wipe data folders and file with a one right-click.
Everyone must have file erasure software.
File erasure software has become an inevitable tool for everyone if you are at an unbroken risk of data stealing and abuse in states that might be out of your control. For instance, sharing your PC, giving it over for advancement or overhaul, browsing the web with no smearing of saved history, sensitive files, and marketing or trading your used gadgets with no smearing can outflow your private data. Get this lab report that summaries research of the universe's biggest sample of total 311 utilized mobile phones, hard drives, and SD cards to disclose that 7 out of 10 gadgets are at danger of data breach and outflow! Never occur prey to monetary frauds, pestering, and chagrin.

More than texting and calling Smartphone's are used in many ways. With the help of the Smartphone's, you all set to access social media, browse the internet, stream video as well as the content. That's the reason mobile phones are at risk. You ought to offer better protection to your Smartphone's.
Installing a VPN will help your mobile phone device to protect in many ways. If you set up VPN software then you all set to secure the upcoming things.
Protect your data:
Once after you install a VPN then all your online activities will be done through that. For sure the data will not escape and none of the people dare to access your data as well. Even an experienced hacker can't able to access your data as the data is encrypted and no hacker can able to decrypt the data.
Safeguard device even surfing online:
Once after you install the VPN software you all set to visit any website. At the same time, you are not allowed to visit the site straightforwardly. Once after you connect with the VPN's server alone you will be able to connect with the website. That's why it is called a secured connection.
You know the VPN server will secrete your browsing history as well from others via hiding your physical location.
Access sites:
The main advantage you want to notice is that VPN won't show you the actual location instead of that it will show some other location. You are all set to access any data without showing your location as well. In case you are the place where some activities such as watching sports are not allowed then you all set to easily access and watch it. Before choosing a VPN make sure that is provided with speed and security.
Mobile phones are no longer used simply for making phone calls and sending texts. In truth, those are probably the least two common uses for mobile phones today. Instead, people use their mobile devices to work, access social media, browse the Internet, stream video content, and more.
And as most people are always on the go, mobile phones are used everywhere. This fact makes mobile phones incredibly vulnerable, which makes it necessary to have as much protection as possible. A VPN, such as the Surfshark VPN for mobile phones, can keep you and your device protected on the go in the following ways:
Secure Your Data
A VPN provides an insulated avenue through which your online activity travels. The data will not escape this avenue, and no one can get into it. In fact, the avenue is nearly impossible to find. Should a determined hacker find the avenue, the data is encrypted so the hacker will not be able to decrypt it. Fortunately, this helps to keep your private information, bank accounts, and more secure, which is needed when out in public.
Use Secure Connection
When you use a VPN to visit a website, you are not connecting directly to the site. Instead, you are connecting to your VPN's servers that provide a safe connection to the website. This hides your browsing history from others while also masking your physical location.
Maintain Privacy
As your browsing history and information do not get collected, they are not sold to third parties or used against you in any way. What you are doing online is kept protected as well as your physical location. These features can protect you from several undesirable scenarios.
Gain Access
As a VPN does not use your actual location but instead the location of their servers, you are not bound to any location restrictions and censorship. Whether you are an activist who wants to remain anonymous, a sports fan who wishes to view content from other countries, or a Netflix user that wants to binge out on content not available in your area, a VPN can make it happen by making it appear that you are in a location where these things are allowed.
Choosing a VPN for Mobile Phones
When it's time to choose a VPN, you should not do it haphazardly. There are several options available, so you need to know what to look for.
Security
The most significant point of a VPN is to provide you with security, so of course, you want to find one that guarantees that. To do so, you need to find one that does not log its user's activities. Unfortunately, some VPNs do keep logs. This is especially true with some of the free options as selling your information is how they make their money. Read the fine print to ensure that the VPN does not keep logs.
Speed
With our mobile phones being used for work, keeping up with family, browsing the Internet, and more, waiting around for content to load is simply out of the question. Some VPNs that do not have many servers actually slow down your loading speeds. A VPN with at least 1,000 servers in several countries will provide good speeds and access to more international content.
Kill Switch
If your connection to your VPN drops, that VPN needs to sever your Internet connection immediately to prevent any chance of vulnerability. Your privacy and data could be very compromised if your VPN connection suddenly drops, and you have no idea. As you continue to use an unsecured connection, it is open season to any hackers, companies, or governments that rely on public Wi-Fi connections and mobile connections to collect your information.
Instead, you need a VPN that protects you even then. A VPN with a kill switch means that if your connection to the VPN drops, it immediately kills your connection to the Internet. When choosing a VPN, be sure that this is one of the features.
Connections
Most people or households connect to the Internet on more than one device at a time. Some might scroll through social media on their mobile phone while streaming a movie on their smart TV. Both parents and children may be using the Internet on different devices. Or you might go to the coffee shop to work on your laptop while your phone is at your side.
Regardless, it is important that you keep all of your devices protected, even when you are on more than one at a time. A VPN that provides several connections means that you can be sure all of your devices are secure. Try to pick one that allows for at least five connections, but the more, the safer you are.
Ease
There is no need for a complicated VPN. In fact, the more difficult it is to use, the less likely you are to use it. Find one that is easy to set up and easy to use.
Just because you are on the go does not mean you have to rely on public networks and risk your security. Do not leave your privacy and data up for grabs. Be sure that you protect all of your devices, especially your mobile phone as it is on the go as much as you are.

Internet fraud has grown and taken different dimensions. As technology advances, so do fraudsters improve their techniques of stealing from individuals. It's prevalent to find unsolicited emails and text messages in your inbox, asking you to provide personal details.
Some of these emails and text messages contain malicious files. The aim is to infect your computer or mobile device and steal personal information.
The best way to ensure your online security is by using apps that protect you from scams. You can find the best collection of apps to protect yourself from spam and fraudulent calls on Appgrooves.
Apps to Protect Yourself from Spam & Unwanted Calls.
I use two of the top apps you'll find on the page, and they've proven very useful to me. While using apps will help, the points below would further guarantee you stay ahead of fraudsters.
Be Careful with Links
Your email service provider might mark a genuine email as spam sometimes. But it doesn't take away the need to be cautious of email messages on your spam folder, or just any new email at all. You should have an eye to spot unusual and unsolicited messages.
Fraudsters often offer cheap products for sale, or pose as a social network provider, and try to lure you into clicking an external link. If you fall for these scam tactics and provide your details on those phishing websites, your information will likely get stolen. You can lose sensitive data or even money from this.
Check links attached to your emails and ensure it's safe to visit. Also, ensure that the websites you visit are generally safe. Download files and software from trusted sites alone as some websites can embed malware in files gotten from their site, and your credentials are their target. Apps are available to help you identify spam websites.
Use Spam Filters and Antivirus
Fraudsters could send spam emails with attachments. These attachments mostly contain malware, targeted at stealing your credentials. Some might install malicious software into your system to enable the fraudsters to monitor your online activities. Before you download any attachment into your computer, ensure such email messages come from trusted sources.
Technology has continued to help us protect ourselves from spam emails and maintain our online privacy. Spam filters can help protect you from spam emails by scanning the emails you receive for malware and quarantine any malicious content in your emails.
If you download malware into your laptops, antivirus software can help you identify and remove such files, and ensure your credentials are safe. It's vital to have these tools handy, and from competent sources, to ensure you're safe. Scan your laptop frequently for malicious software and files, and follow the instructions of your antivirus software to deal with any identified malware.
Use Call Identifiers
Fraudsters are not limited to emails and text messages. Some can go the length of calling their target on phones and posing as agents of various trusted agencies or financial service providers. They might even offer to help you with certain products or services.
Most times, you might receive the call from a cloned phone number and think such requests or offers to assist you are coming from trusted agents. It's safe to be skeptical of calls from an unknown number. Don't be quick to provide sensitive information to such callers, except you're sure of the request.
Using call identifiers can help you identify who your actual callers are, and their location. Appgrooves has a collection of apps that can help you track the source of any unknown calls you receive.
Conclusion
Identifying and dealing with fraudsters can prove challenging. The importance of being cautious is paramount. Using apps and software can make it easier to identify and effectively deal with cheats. Get apps and software that best serve this purpose and be completely protected.
© 2023 YouMobile Inc. All rights reserved





