Search result
 |
 |
|
this article is not available |
||
 |
 |
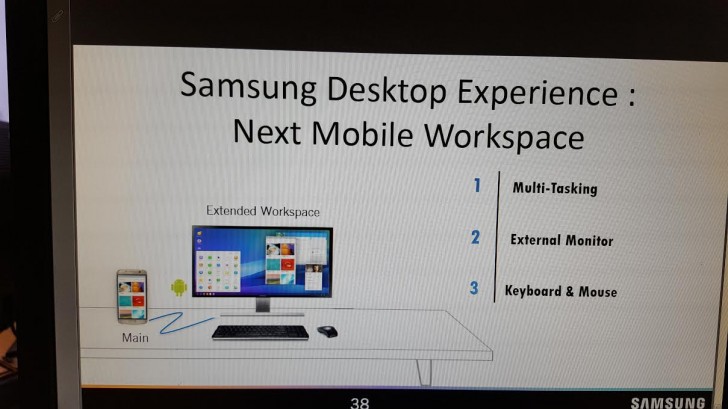
We are already into 2017 and the Galaxy S8 may not seem as far away from being launched as it seemed to be just a month ago. Today, a new report/leak has come into attention, courtesy of an unlikely source; allaboutwindowsphone.com. What we can see via the leaked image is a software running on a PC, called Samsung Desktop Experience. There are three visible tabs on the right, marked as,
1. Multi-Tasking
2. External Monitor
3. Keyboard & Mouse
As some of you have already figured out, the entire setup looks very similar to Windows Continuum Workspace experience, reserved for Windows smartphones only. As the Continuum program allows a Windows smartphone user to experience PC-like functionality, we are guessing that the Samsung Desktop Experience will also bring something similar to the Galaxy S8.
The only issue might be that the S8 will run on Android, which is a completely different OS from Windows altogether. Nevertheless, I am sure that Samsung will hire the right developers to bridge the gap in-between the two operating systems in order to deliver a smooth experience to the users. The ability to properly use a keyboard and a mouse could lead to windowed apps, true multitasking and better productivity on the Galaxy S8 in certain situations. Are you excited for his one?
Saikat Kar (tech-enthusiast)

We all are using 4G LTE devices now, However, the International Telecommunication Union (ITU) is working on setting the standard and defining the specifications for the Next Generation 5G (5th Generation) Network.
Between June 10th and 18th, 12 delegates debated on the specifications to be established for the upcoming 5G network standard. The ITU has decided that 5G networks will have a peak speed of 20Gbps, or 20 times the peak speed specification of 4G LTE networks, which stands at 1Gbps.

One thing to bear in mind is that these are theoretical max speeds, and that the first 5G networks will likely reach much lower peak speeds. At the moment, the fastest LTE standard is LTE Cat 9, which provides peak speeds of up to 300Mbps, well below the 1Gbps speed specification of 4G networks. What this means is that while crazy transfer speeds are to be expected, 5G subscribers will not be able to download an ultra high-definition movie in just a second, which is what a download speed of 20Gbps would mean if put into practice.
5G networks will also be built with internet-of-things (IoT) devices in mind, as the ITU has established that 5G networks will be able to cater to more than 1 million IoT devices inside a 1 square kilometre radius at an average speed of above 100Mbps. The ITU expects the first commercial 5G networks to start opening for business in 2020, although a working example is being prepared for the upcoming 2018 PyeongChang Olympic Games.
© 2023 YouMobile Inc. All rights reserved





