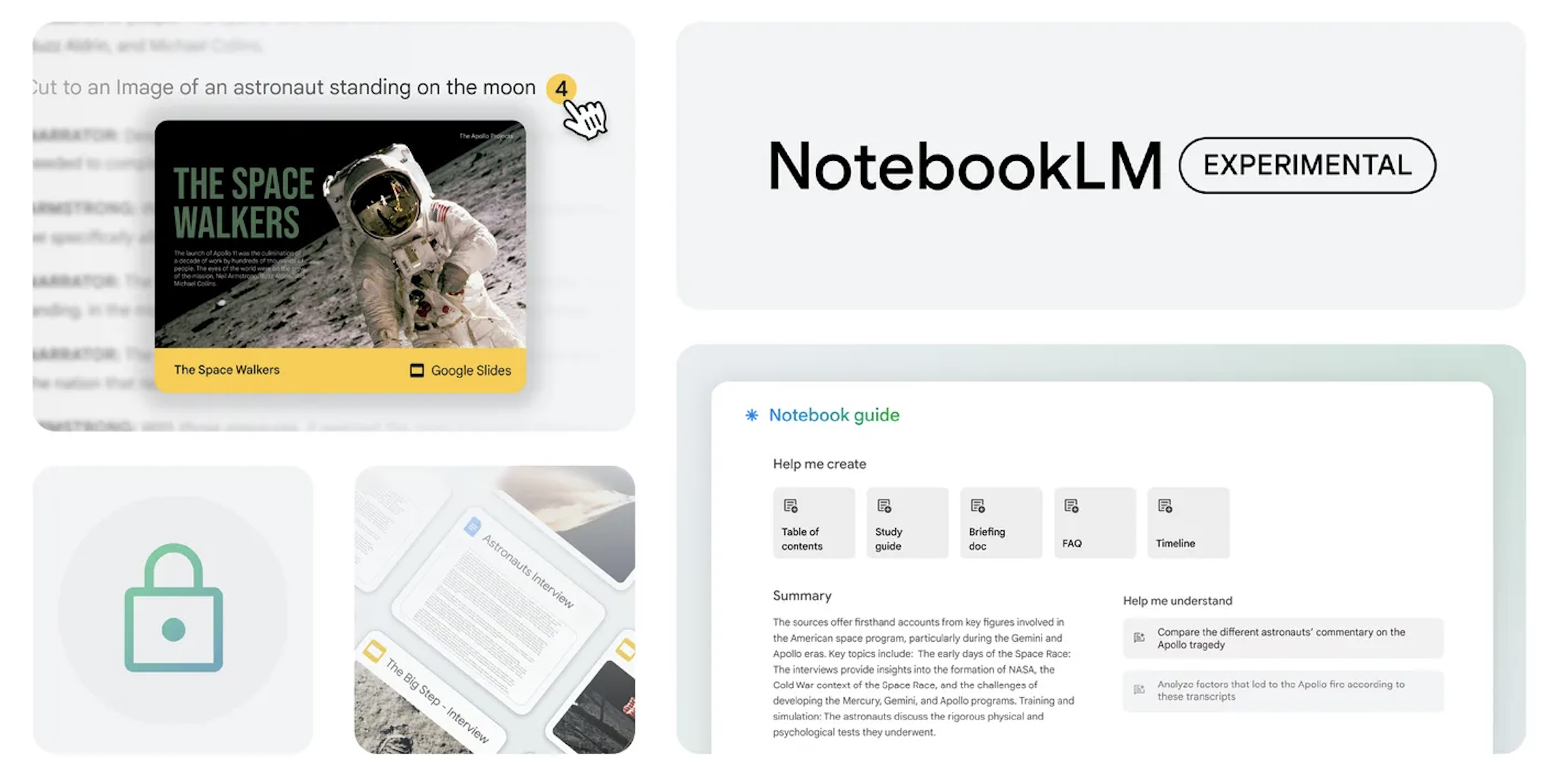
A while back, Google announced that it would be bringing Gemini 1.5 Pro to NotebookLM, a smart assistant platform where users can upload documents and use AI to summarize content, pose questions and more. There was also talk of bringing over NotebookLM to more regions worldwide - as such, it looks like Google has made good on its promise following a more recent announcement.
The company finally announced that it has brought over an upgraded version of NotebookLM with Gemini 1.5 Pro to over over 200 countries and territories around the world. Part of Google's announcement reads:
Our goal from the beginning with NotebookLM has been to create a tool to help you understand and explore complex material, make new connections from information, and get to your first draft faster.
With that being said, users can now upload their sources including research notes, interview transcripts, corporate documents, which will serve as a foundation for NotebookLM's knowledge base for users.
With all that said, users will be able to incorporate content from Google Slides and web URLs alongside previously supported formats like Google Docs, PDFs, and text files. Additionally, NotebookLM now offers inline citations that link directly to the relevant passages in source documents, allowing for effortless fact-checking of the AI's responses and deeper exploration of the original text.
Finally, there's also a new Notebook Guide, which automatically converts source materials into user-friendly formats like FAQs, Briefing Docs, or Study Guides, providing a comprehensive understanding of the information at hand. Users can also ask questions about images, charts and diagrams in their sources, and NotebookLM will include citations to images as supporting evidence when relevant.

In less than the space of a year, Zoom has managed to become one of the most ubiquitous communication tools. Indeed, like Google, it has reached the ‘verb' status. Just like we talk of googling something, we also use phrases like zooming and zoom as synonyms for video calling. It has become a massive company overnight, a stock market darling - but it's not for everyone.
Below we want to set out five reasons why you should switch from Zoom to alternative video conferencing software. The object of the exercise is not to say that Zoom is poor (it has its plus points), nor is it to venerate another video conferencing. Rather, it's to offer a broader view, particularly as the media has given Zoom an almost de facto status as the only video conferencing option.
There are many alternatives to Zoom that have become important tools for communication during the pandemic. An option like the Spike email app for Android is perhaps not the first thing you think of when it comes to video conferencing, but it has excellent video conferencing tools that forms just one aspect of the overall product. The point is that Zoom did not invent video conferencing software, and nor should you be obliged to think narrowly about the options you have for video conferencing.
Regardless, we wanted to look at five reasons to consider switching from Zoom to an alternative. These are set out below:
Security Issues
It's over a year now since the first major security issues with Zoom made the headlines. The company spent a lot of time, money and effort to fix them, and it went on a PR blitz last spring and early summer to assure users (and investors) that they had been addressed. However, several security issues still persist. Indeed, it was demonstrated in April 2021 that a hacker could hijack PCs and Macs using an unknown security flaw in Zoom's Desktop Client. Most of last year's problems - "zoombombing", lack of two-factor authentication, and end-to-end encryption - have been fixed, but other problems persist.
Competitors Have Improved
To be frank, one of the reasons Zoom has become so universal is that it was one of the first companies of its kind to truly see the opportunity (we use that word respectfully) of the pandemic. Its prescience over remote working culture allowed it to capitalize on the boom. And, to be fair, it quickly added new features and tried to update its security flaws. But others, like Cisco Webex and Teams, have caught up recently, and they are pouring money and resources into improving their platforms in the knowledge that remote working won't disappear after the pandemic.
All-in-One Alternatives
Everyone knows what Zoom is - video conferencing software. Effectively, it does one thing - and it does it well. However, many alternatives do more than one thing. We mentioned Spike above. It is a collaborative tool integrating email and chat functions, among other solutions for productivity. Video conferencing is just part of its offering. Teams, too, sees video conferencing as just one aspect of its overall product. Zoom has some extra features, but video conferencing is its raison d'être. Why use multiple tools for collaboration when you can have them all in a single application?
Integrations and Collaboration
Much of this section is to reinforce the last point made above, but it is important to stress how some of Zooms competitors go beyond it in terms of integrations. We don't want to sell Zoom short. You can, for example, use Zoom add-ons to enable meetings through platforms like Slack. But other options have built their own ecosystem to integrate other products seamlessly into video conferencing, meaning you don't have to open - and pay for - separate applications and software for file storage, email, and so on. Teams, for example, is able to integrate its Office 365 stack, whereas Zoom will have to rely on third-party applications. Zoom has yet to build such an ecosystem, but others have put it at the heart of their product.

The Internal Question
We mentioned that Zoom has risen to the fore during the pandemic, and it should be rightly applauded for predicting how crucial remote work collaborations would become. However, there is an assumption among some experts that we will be returning to the office en masse. Remote working will still exist, but not on the scale we have seen in 2020 and the first half of 2021. Many experts believe that Zoom is superior as an external tool, i.e., for remote working, whereas its competitors are superior for internal, office-based work. You can see the logic, given that Zoom was forged in the cauldron of the pandemic during the exodus to the home office. The real test for Zoom might be when return to office life.

Recently I needed to check the IMEI of my iPhone, so I went to look for some useful and free tool that can help me with this. So I came across a very decent iPhoneIMEI.net service. In this article, I will tell you what information you can get with this tool and why you need to check your IMEI at all.
What is IMEI and Why Do You May Need Check it for iPhone?
IMEI is a unique phone identifier consisting of 16 digits. It is applied to its packaging, case and battery, and is recorded in the operating system (so you can find it in the settings).

When you buy a new iPhone, you need to register it and do it by entering the same IMEI. That's why it's useful to check iPhone IMEI - it's the most reliable way to find out if the phone is really new and official.
What You Can Learn Through iPhoneIMEI.net Service
Tool iPhoneIMEI.net shows a lot of information about the device, not just writes whether it is an official phone or not. For example, you can find out what country this iPhone is registered in, whether it is still under warranty, and in what year (and even what date and month!) it was sold. The service will be useful both for those who buy a new iPhone and want to make sure that it is really new and for those who are going to buy a used phone and are worried about its usability.

The warranty information will also come in handy if you have been using your iPhone for a long time and you need to fix it badly. Also, iPhoneIMEI.net says the date when your device's technical support expires.
A complete list of the data that the service shows is available at https://iphoneimei.net, right below the form where you need to enter your IMEI.
Even more features and capabilities are implemented in the Premium version.
The interface of the tool is also worthy of attention because it is as simple as possible. I didn't have to search long for how, where and what to enter, and the list of information immediately made me realize that this is exactly what I needed.
See for yourself; everything is implemented as clearly as possible. To access this form, you do not need to register.
By the way, if you don't know where to find your IMEI, the service also tells you how to do it. I duplicate the information here: besides the check on the box or the case, you can just enter *#06#.
Among the shortcomings of the service, I could name a limit of one check in one day, but I am not sure how serious this flaw is. Hardly many people have more than one iPhone, and they need many checks every day.
To make a brief conclusion, I definitely recommend this decent free tool to check the IMEI of your iPhone.
Mobile apps have revolutionized business. Transactions have been simplified, and brands can communicate with their customers directly and in a personalized manner. If you have a business - regardless of size - pairing it with an app is something you should give serious thought to. The digital age has provided a level playing field for all brands, and standing out has become incredibly intricate. Read on for ways an app can better your service delivery and give you the edge on your competitors:
- An app provides you with a free marketing channel
One of the most significant benefits of having a business app is the ability to communicate directly with your customers without competing for attention. Your app carries only information about your brand and product. This means that when a customer opens it, there is zero chance they are there for anything but information about your product or service. Your only job is to ensure the information you provide is relevant, useful, and, if possible, personalized.
-
Apps separate the great from the good.
Apps are everywhere these days, but don't let that fool you: most of your rivals don't even know their businesses can use an app. You can use the opportunity to leapfrog them and pull yourself closer to the market leaders. Your customers will love your innovativeness, and your brand will take on a new look of credibility and classiness.
But there is a catch to it; a bad app is worse than an absent app. If you are going to develop an app, ensure it is terrific because such a significant addition can only enhance or break your business. Get a seasoned developer to build the app for you. Goodcore is an app development company based in London with a team of experts specializing in different aspects of app development. This is the expertise and level of dedication that you need for your project.
-
A business app will increase customer engagement.
All clients need a clear communication channel with the provider of the service they are seeking. If customers can't reach you, a chunk of them will likely consider the next brand. Mobile apps enable this reach. You only need to create a section on the app where customers can interact with the support team and chat. A mobile app eliminates the need for customers to visit your website to interact with the business or get more details.
-
It increases customer loyalty.
Customer loyalty is achieved when you keep reminding your customers that your brand exists. Then again, everyone uses the same channels to elicit commitment - banners, flyers, flashing signs, newspaper ads, roadside banners, billboards, social media, email, coupons, etc.
You cannot draw on these hackneyed means and expect to realize extraordinary results. A mobile app will help you connect with your clients in a way that makes them feel valued. Gradually, they will develop an attachment to your business and potentially turn into your brand's self-appointed ambassadors.
-
Build brand awareness
Among the crucial things an app offers to consumers is communication with and awareness of your brand. It offers a platform for regular interaction with the target market, which helps to foster loyalty and trust. Also, when a customer is frequently exposed to your brand, their buying intent increases. That's why mobile apps are considered an effective brand promotion strategy. A mobile app is one of the best tools for enhancing brand visibility.
-
On-the-go advertising
Whether they are at a coffee shop, at work, or in a traffic jam, a mobile app allows consumers to access a user-friendly place for your business. The regular use and easy accessibility help to reinforce your brand and business, increasing the possibility of consumers making purchases.
-
Easier market research
If you have been running your business for some time, you know how market research is crucial to businesses. A business app makes it easy to conduct market research. It makes it easy to collect, analyze, and leverage consumer data. Capturing consumer insights such as consumer preferences and behavior can help you make the right decisions and focus your energy in the right place. Therefore, with a business app, your business can use data-driven marketing statistics to offer customers a personalized experience.
-
Mobile payments
Mobile payments are a secure means of transaction, and they have been growing in popularity. Customers are not required to share any sensitive information, and thus there is no possibility of a third party accessing the information. Integrating your business app with mobile payment will make customers feel secure about their private and transaction information.
-
Worldwide audience reach
Most people around the world access the internet through their mobile phones. There are over 4.5 billion active internet users around the world, and most of these people access the internet through their mobile phones. A business app increases your business's global reach.
-
Value creation
A mobile app will make your services or products more trustworthy for consumers. 94% of the top 50 retailers in the United States have at least one mobile application. A mobile application also makes your business look more professional.
-
Maximize sales and revenue
The flexibility offered by mobile apps has led to increased mobile app transactions in recent years. They offer a convenient, simple, and intuitive purchasing process, which is why most customers prefer them. This helps to improve customer experience, which positively impacts sales.
-
Brand endorsement
A mobile app will help you create a good reputation. You see, nobody wants to buy something without reading comments and reviews from other buyers. Just like you wouldn't go anywhere without checking ticket pricing, routes, and hotels beforehand. Positive reviews by your existing customers are an effective way to attract potential customers.
Conclusion
There are many ways to upgrade your business. Creating an app, albeit relatively costly and time-consuming, is one of the most viable ones. Don't ponder it a minute longer. Develop a business app today and see your brand take on a new fast-tracked growth curve.
Many IT specialists are stuck in low-paying and boring jobs. Why? Most of them are just unwilling to update their technical skills toget ahead in their careers. And as a result, they are struggling to keep pace with the latest trends because they haven't observedthe recent shift to new www.certbolt.com.
It's important to understand that theglobal workforce is quickly evolving. Companies want to achieve more with the least resources and its only right that you unlock your full potential by improving your skills. Today, we are going to show you how you can achieve more in the networking field by adopting the right study approach. Here's your guide to the Cisco 300-415 exam and what benefits it can bring you.
Cisco 300-415 Exam Overview
Taking effect from February Cisco 300-435 ENAUTO CCNP Certification Practice Questions is part of the new Cisco certification path, keeping up with advancements and market demands. This exam, formally named Implementing Cisco SD-WAN Solutions validates your knowledge of SD-WAN Architecture, Router Deployment, Security and Policies, Controller Deployment, Operations, and Management. These are however merely guideline areas, so don't hesitate to visit the official Cisco website to know all the topics in detail.
The assessment is associated with the CCNP Enterprise credential but you must also pass the Cisco 350-401 exam to earn it. Sitting for 300-415 test separately, you'll not verify your professional-level skills but still will acquire a certification, namely Cisco Certified Specialist - Enterprise SD-WAN Implementation.
Requirements for Cisco 300-415
The candidates for 300-415 should have mastered all the topics mentioned in the exam outline and have experience in CCNP Enterprise Certifications Exams & Deployment. Besides, the applicants shouldbe familiar with wide-area network design and routing protocol operations. These are not prerequisites for the test but are foundations upon which itis built.
What Do You Stand to Gain?
For system integrators, network administrators, and solution designers, the benefits of passing Cisco 300-415 are huge, as it is essentially a mark of quality in their niche. Itprovides thorough and rigorous coverage of the basic and advanced concepts. Also, higher qualifications come with better pay among other opportunities: as stated at PayScale.com, professionals with CCNP Enterprise can expect to earn about $95k annually on average. So, the doors opened by the Cisco 300-415 exam will give you value for Click Here to Visit Resource URL.
Your Best Preparation Tip
Cisco offers a course to prepare you for the exam, entailing three options: guidance by an instructor, lab practice, or purchasing self-study materials. However, this may not be enough as long as it's also important to know how the exam is built and what questions might await you. For this purpose, acquiring practice tests from a reliable provider can help.Training with these materials, remember to correct all the mistakes and time yourself to improve your exam-taking speed. After such trial attempts, you'll be ready to ace your main Vist Web Site URL Here Now.
Conclusion
Our modern IT market thrives on competition, and the more qualified you are, the higher the demand for your services. The final result is improved wages and multiple options for career advancement. Being a universally recognized certification exam, Cisco 300-415 will stretch your boundaries and get you going towards this goal. Take charge now, prepare thoroughly with practice tests, and get your Certbolt Cisco 300-420 ENSLD Exam Dumps!
© 2023 YouMobile Inc. All rights reserved





