Search result
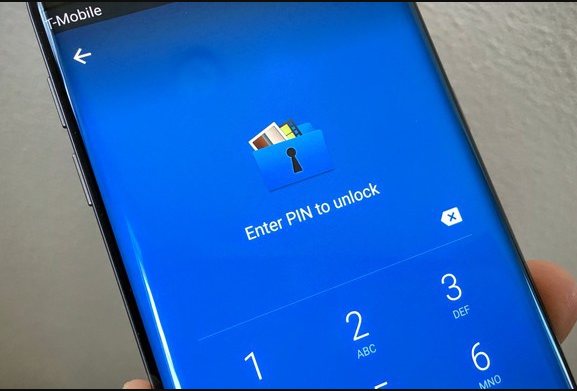
You can now download and install the Secure Folder application from the Galaxy Apps Store. Unfortunately, the only two devices supported officially at the moment are the Galaxy S7 and S7 Edge. Support for more devices is incoming though, as confirmed by Samsung. It should be noted that the upcoming Galaxy A (2017) series of smartphones will launch with the app pre-installed. Post the Nougat update, the S6 series and the Galaxy Note 5 too should be able to use Secure Folder without any issues.
Secure Folder is an application that brings personal security to Samsung smartphones. Anything the user does inside the Secure Folder remains secret and unavailable to everyone else who does not have access to the app. Everything from pictures, videos, documents and even apps within the Secure Folder is private and inaccessible without access to the app first. This enables users to create multiple accounts on applications like whatsApp, which would not let you operate two accounts from one phone under normal circumstances. If you have a S7 or S7 Edge, give it a try now. If you don't have one, just wait until Samsung expands the support further to your smartphone model.
Saikat Kar (tech-enthusiast)

The Galaxy S8 and S8+ showcase an arguable design choice when it comes to the location of the fingerprint scanner. If you are a lefty, reaching it will be tough on a regular basis and even if you are a righty, you may end up smudging the camera lens much more than you may like to. However, as it turns out, the facial recognition feature is blazing fast in unlocking the phone on both the devices. While this does make up somewhat for the oddly positioned fingerprint scanner, the feature isn't as secure as we would have liked it to be.
The lack of security in using the facial recognition system was made apparent by a Twitter video uploaded by MARCIANOTECH (@MARCIANOPHONE). It seems that the Galaxy S8 smartphones are not impossible to unlock even when the face is different and that's not good news for a feature that Samsung has been advertising as one of the main attractions for the Galaxy S8. It is possible that Samsung will be able to fix it by the time the handsets are ready to be shipped to their customers, or maybe they can just release a software update later to take care of it. We will have to wait and see what happens.
Saikat Kar (tech-enthusiast)

Technology has grown to occupy a central place in society and play a key part in all our lives. Of course, some technologies are more common in everyday life than others and have a significant impact on how we live. Mobile tech is a great example of this. Smartphones are something that we all rely on now. Whether it is making calls, catching up on emails or surfing the web, these devices are crucial to most people around the world.
The variety of things we do via mobile devices now means that the security features they contain are more crucial than ever. This includes examples such as facial recognition software, which ensures that only the right person can access a device, and mobile network security, which keeps hackers at bay.
This kind of security is essential for mobile devices, as they contain so much of our personal data, banking details, email messages and private photos. If these kinds of things were not available, people would not be as comfortable using them and they would not protect users in the best way.
The importance of secure coding practices for mobile apps
When it comes to making mobile phones safe for people to use, secure coding practices are also something that prove invaluable. This refers to mobile app developers using techniques when coding their applications that make them extra safe to use.
As apps are popular with all mobile phone users, producing those that are coded in an ultra-secure way makes sense. This not only makes it harder for online criminals to breach app security but also gives people full confidence that the apps they use are secure.
Cyber security specialists and secure coding practices for mobile
The seriousness of security for mobile devices is causing people to predict that the cyber security students of today will be at the forefront of the sector moving ahead. This is because these students learn not only what common online dangers pose most problems to mobile users, but also which security weaknesses hackers might target in an app or mobile phone.
They can then use this knowledge to design mobile devices that provide much stronger protection against hackers and apps that utilize the latest secure coding practices to deter online criminals. In terms of mobile apps in particular, techniques developed around secure coding within cyber security can be directly transferrable to creating safer applications.
How do you become a cyber security specialist?
The above shows that training to become a specialist in cyber security could lead to decent employment opportunities in the mobile sector. As things such as secure coding practices become more important in mobile phone apps, people with specific skills in this area are in demand.
The online nature of modern society also means that people with in-depth knowledge of online security are in demand across a range of other industries. This can be businesses in any sector that have an online presence and need someone who can safeguard their network, protect their databases and help them work securely in the cloud.
Due to this, training to work in cyber security is a popular career choice.
If you are wondering how to become a cyber security specialist, the best place to start is getting the right qualifications. The Master of Science in Cybersecurity from St. Bonaventure University is a popular course in this field and perfect if you like the flexibility of online studies. This program teaches students all they need to know about helping businesses stay safe from online threats. This includes learning around secure coding practices, cloud security, machine learning and data mining.
What skills do you need to work in cyber security?
Cyber security is a field where academic qualifications are not the only driver of success. If you plan to move into this employment sector to build secure apps or make mobile phones such as the Apple 1Phone 14 Pro safer, you also need the right skills to call on.
The most important ones for specialists in this sector include:
- High-level IT/computer skills
- Problem-solving
- Communication
- Organizational skills
- Multi-tasking
- Leadership
- Programming
- Analytical skills
- People skills
Although the above list does not show every single skill that can help you succeed in cyber security, it gives a flavor of those that are used most regularly in roles across the industry. By working on these skills, you can not only succeed in your career post-graduation but also become more attractive to potential employers.
What type of person should move into cyber security as a career?
People who are interested in computers, technology and online/mobile tech are all ideal candidates for this sort of career. This sector can also be a good fit for anyone who loves to work independently at times and use their knowledge of IT to solve cyber security issues. This could involve building impenetrable digital fortresses to keep out hackers or enjoying the thrill of responding effectively to a sudden online threat.
Of course, if you already work in IT or other fields based in computer science, then you may also find working in cyber security interesting. It is key for all cyber security professionals to enjoy keeping up to date with the latest industry trends (such as secure coding practices) and emerging online dangers. This enables them to use this knowledge in their own role and fulfill their duties effectively.
What roles do specialists in cyber security typically move into?
Cyber security is actually a wide-ranging term. There is a great range of individual roles within the sector that people can move into. These include:
- Security architect
- Network engineer
- App developer
- Solutions architect
- Lead software security engineer
- Information security analyst
- Chief information security officer
When it comes to cyber security for mobile phones in particular, app developer is one specific role that stands out for graduates. If you like the thought of helping to design apps that are ultra-secure, then it could be the perfect job for you. Secure coding practices that cyber specialists develop are crucial to working in this position and creating robust apps.
But how do cyber security experts develop these types of coding practice?
Security testing
Although there are multiple ways that specialists in cyber security develop secure coding practices for mobile apps, a focus on security testing is one of the most important. This refers to mobile applications being thoroughly tested to ensure that they are safe to use and provide excellent security against hackers.
By doing this, the app developers are able to code products that have been properly tested for high-end user security and products they feel confident are secure to use on a global scale. Security testing also enables those involved with mobile app development to spot any glaring security errors in the product’s coding and across the application in general.
A good example of this would be performing periodic vulnerability scans on the app in order to identify code that might be vulnerable to attack. It is also possible to use automated source code analysis to spot any security flaws in an app’s coding.
Security patches to fix coding issues
It is crucial to point out that there may not have been any security issues with an app before it was rolled out. However, there are always new online threats emerging that see hackers finding fresh ways to get past previously secure app defenses. Once this happens, it is vital for app developers to work quickly to make security patches available to users and plug any vulnerabilities.
This is something that cyber experts have helped to popularize, and they continue to work with the mobile industry to help it respond to emerging threats from online criminals. It is common for these security patches for apps to rely on amendments to code and for extra layers of security to be added into the source code of an app to make it safer. It may also involve removing code that has been exposed by hackers or that has become a security weakness.
Authentication of certificates
Authentication is another valuable technique for secure coding and creating robust mobile apps. This refers to developers using specific software in their apps to validate the contents of an online certificate. These certificates are digital documents that confirm the true identity of a website or server. The certificate itself includes key data about who issues the document and which hostnames are connected to it.
By using software such as NSURLSession or HostnameVerifier, app developers can authenticate certificate contents from users and reduce the danger of certain attacks (such as so-called man-in-the-middle attacks). These sorts of attacks can be serious, as they amend the communication between the server and the app itself. This can then enable cybercriminals to access the app’s code and make changes to it or alter certain app features. By authenticating certificates, the app becomes safe for genuine mobile users to download and is kept safe from cybercriminals.
Biometric data storage
As we have already noted, biometrics is a major trend in mobile development and enables people to use unique personal data to access tablets, smartphone and apps. Good examples of this in action include facial recognition scanning on mobile devices and fingerprint scanning. Although this data may be unique, it still needs to be stored on mobile devices and apps for them to recognize who is trying to access them.
As with any kind of data storage for sensitive information, it is key for biometric data to be safely looked after for mobile users. Cyber specialists have been instrumental in developing techniques that enable this and allow biometric data to be used safely in the mobile sector.
A good example of this is how the technique of hashing was developed in the cyber security industry to help store this sort of information safely on apps and mobile devices. This involves turning biometric data into a string of code that is hard for unauthorized people to decipher. Hashing is also widely used in the mobile world to store unique personal data, as it stops this data from being matched with other sources online to authenticate it. Code obfuscation is another widely used technique in this area that was developed by cyber experts. This sees the code structure/syntax amended to make the data complex for hackers who do not know the rationale behind these changes.
Data encryption
Another useful secure coding practice for mobile apps developed by cyber experts is data encryption. This is useful for app developers, as it allows any sensitive data stored on an app to remain safe from hackers. This is because encrypting data takes the raw user information that an app might hold and jumbles it up via a high-end computer algorithm.
This encrypted data to be stored on the app is extra secure and almost impossible for anyone without the correct encryption protocol to decrypt. As you can imagine, this technique around app safety is much better than simply storing sensitive data without any kind of encryption to protect it. If this were to happen, any hacker who did breach an app’s security features would have access to a wealth of personal user information in its rawest form.
Avoiding hardcoding of things such as APIs in the source code of an app also means that hackers cannot steal key data if they manage to obtain the application source code. When combined with cryptography in app creation, this allows developers to create products that are able to resist common threats such as side-channel attacks. As a result of the above, the app’s code is kept much safer and the data on an app is kept more secure – even if online criminals were to breach the application’s initial security features.
Authorization
A key element of mobile app safety is that only authorized users should be able to access an application. This, of course, is also something that is key for mobile devices in general, where only the owner of a tablet or smartphone should have access to it. When you think of the wealth of sensitive data on our apps and phones, this makes perfect sense.
Good practice in terms of secure coding that cyber experts have developed is therefore key for app authorization. This sees apps created in such a way that people have to sign in first and confirm their identity before being able to access them.
App authorization through secure coding on a more general scale is also interesting to note and something that cyber experts have helped to develop. This sees the code behind an app written in a way that only allows users to access certain parts of the app. As a result, it stops people getting to parts they shouldn’t have access to and unauthorized people from getting up to mischief (such as stealing data or changing the application’s code).
What’s next for cyber security within the mobile world?
There is no doubting how important online security is to the mobile sector and what a great job secure coding practices do at keeping mobile users safe. Due to this, it is almost certain that cyber security will continue to play an increasingly key role in the mobile phone industry. But how might this look as we move forward?
If we look at applications specifically, you expect that online security experts will continue to find new ways to secure the data that applications collect and store. This could involve higher levels of data encryption and new algorithms that help facilitate this.
For mobile devices in general, it would seem certain that cyber security specialists will continue to develop new techniques in areas such as secure coding to make them safer. This could involve the next generation of phones having ever more sophisticated biometric access protocols or the new wave of tablets running on network security processes that are almost impossible to breach.
Secure coding practices are key for mobile phones
People will only continue to use mobile phones if they feel that it is safe to do so and they are designed in a way that keeps online criminals at bay. One very effective method to achieve this is through the secure coding practices that cyber security specialists have developed for use with mobile devices. By developing and helping to implement these practices, cyber specialists are able to make mobile phones and apps a lot more secure to use.

Betting is a game of both luck and chance, but this doesn't mean there aren't a few helpful tips to better your luck at the online casino there are many things to do that can give you better odds of logging off without big losses.
If you are new to the wonderful world of online betting this little guide can help transform your betting skills and give you a few dos and don'ts when it comes to online casinos. Online betting platforms have become wildly popular and are all over the internet offering great deals and are just a click away, all you have to do is click here to start the fun.
Keep an Eye on Your Money
Playing casino games is meant to be nothing but fun but it has often come under scrutiny due to the ability for it to become out of hand as people taking part can often forget that the money they are placing down is money they need. This is why it is so important to keep track of your spending but luckily when betting online this is made much easier as your bankroll is constantly displayed whilst playing allowing you to keep track of how much one how much you spend and how much you currently have.
When placing a bit handy tip is to ask yourself if you can afford to lose the money you are placing down as opposed to winning the money that is up for grabs as thinking of the worst scenario allows you to plan better. Frequent Or professional better is to set themselves budgets that can be in separate accounts or just a well thought out financial plan to ensure that they know how much they can post down in a single night all week preventing them from delving into money they need for everyday essentials. Do not damage the fan that can be had on betting by allowing yourself to get out of hand, always be smart.
Hit the Books and Know the Rules
Many casino games can appear confusing and this can cause newbies to avoid certain games, but do not be put off as many are much simpler than you may think.
Blackjack is the most popular casino game but can be intimidating for new players as the rules can be confusing because it differs to other games in casinos, this is because it is not as dependent on luck, more so the decisions made by players. The aim of the game is simply to beat the dealer to 21 without going bust. This game is full of thrill and perfect for those who like to be put under pressure as it is ever-changing and rapidly played.
Roulette is another popular game and one of the simplest to play as all you need to do is pick a number, colour or section to place your chips on and wait to see if you are lucky enough for the ball to land on your choices. Winnings differ depending on how likely your choices are to come up and so a single number offers larger returns than colours or sections.

In today's digital age, mobile gaming has become incredibly popular, providing millions of users with a convenient and immersive gaming experience right at their fingertips. However, with convenience comes the potential for cybersecurity risks. As a mobile gamer, it's crucial to adopt secure web practices to protect yourself as well as your devices from potential cyber threats and ensure a safe and enjoyable gaming environment.
In this article, you will find 6 foolproof measures to ensure the utmost security when gaming on mobile.
1. Stay Updated
One of the most critical steps in ensuring security while gaming on your mobile device is keeping your operating system and gaming apps updated.
Developers often release security patches and updates to address vulnerabilities and enhance overall security. Regularly updating your mobile device and gaming applications will help safeguard against potential attacks and ensure you have the latest security features.
2. Strong Authentication
Implementing strong authentication measures is another crucial aspect of secure mobile web practices in gaming.
Implementing strong authentication is crucial in guaranteeing data security. It is imperative to enable Two-Factor Authentication (2FA) or Multifactor Authentication (MFA) whenever feasible, as it necessitates an extra verification procedure beyond passwords ensuring that only you can access it. This additional safeguard greatly mitigates the threat of unauthorized entry into your gaming accounts.
3. Secure Payment Options
Another necessary mobile practice when browsing and visiting gaming websites or downloading mobile gaming apps is to check for the app or the site’s payment options.
In the realm of mobile gaming, in-app purchases are a predominant feature, allowing players to acquire virtual goods and upgrades. Since these transactions may involve sharing credit card details, it is imperative to provide secure payment options. A gaming platform that ensures secure payment processes not only fosters trust and confidence among gamers but also enhances the overall user experience.
For gamers who value their hard-earned winnings, generous bonuses, and cashback rewards, it is imperative to choose a gaming website that prioritizes secure payment options. One such website that guarantees the safety of your funds and even your precious free spins is the casino gaming sites. Don't compromise your peace of mind—opt for the safest online casinos that provide top-notch security measures for all your financial transactions.
Furthermore, adhering to stringent security practices is crucial for gaming companies to meet data protection regulations and legal obligations. Neglecting these measures could lead to reputational harm, legal ramifications, and financial penalties.
4. Be Cautious with Third-Party Apps
While it is tempting to explore alternative app stores or download unofficial gaming applications, it is essential to exercise caution.
One of the primary risks associated when browsing game applications or web sites are malware and data leak concerns. To avoid network disruptions and even financial losses, it is best to stick to trusted and reputable app stores like Google Play Store or Apple App Store when browsing for mobile games, as they have mechanisms in place to detect and remove potentially malicious apps.
Unauthorized or untrusted apps can carry hidden malware that can compromise the security of your device and personal information.
5. Avoid Public Wi-Fi
Public Wi-Fi networks may seem convenient and widely available for mobile gaming, but they can be a breeding ground for hackers and cybercriminals.
For most experts, public Wi-Fi networks are usually unsecured or use weak encryption protocols that might make it easier for hackers to intercept sensitive data transmitted between devices and access personal information.
These public networks, generally, have weaker security measures as compared to private ones and are therefore easy to be exploited for their vulnerabilities. As such, it is recommended to avoid connecting to public Wi-Fi networks when gaming or, if necessary, utilize a virtual private network (VPN) to encrypt your connection and enhance security to enjoy a secure gaming experience.
6. Mind App Permissions
When you download and install gaming apps, it is crucial to be vigilant about the permissions they request.
Some mobile gaming apps might ask for access to unnecessary information or functions on your device, which should raise concerns. It is important to only grant the essential permissions needed for the app to work properly, reducing the likelihood of data breaches or unauthorized access. This can include permissions to access your contacts, location, camera, or even microphone.
By carefully reviewing and limiting the permissions you give to gaming apps, you can help protect your personal data and privacy.
Final Thoughts
Secure mobile web practices are vital to preserving your privacy and protecting your personal information while enjoying the world of mobile gaming.
By staying informed, updating software regularly, employing strong authentication measures, and making informed choices about app downloads and secure network connections, you can create a safer gaming experience for yourself. Remember to always err on the side of caution and prioritize your online safety.
With these practices in mind, you can embark on your gaming adventures with confidence and peace of mind.
© 2023 YouMobile Inc. All rights reserved





