Search result
In today's world, every windows user wants to get their hands on the latest windows version available i.e Windows 10.
No doubt it is really convenient for users to keep their personal files and folders after upgrading but it is not in the case with all the apps and software installed.
An EaseUs software named EaseUs Todo PCTrans Professional 11.0 helps you to perform an in-place upgrade in Windows 10 without reinstalling all apps.
It is a simple to use PC data transfer software (software de transferência de PC) which gives you the ability to transfer applications and personal files between windows operating systems.
You can seamlessly move all your essential data to the new version of your PC which saves you the time and energy to manually copy and paste.
It supports different windows version like Windows XP, Vista, 7,8,8.1 and 10 (32 and 64- bit).
What is does is that it automates the configuration of apps on the new version of Windows with removing the old versions.
INTERFACE
EaseUs Todo PcTrans Professional 11.0 has a very organized, user-friendly and easy to use interface.
It has different steps involved in the whole procedure of transferring data and the interface remains the same in all the steps.
You just need to select one of the given options in each step. If there is some setting change you want to do you can do that according to your preference and rest the program will take care for you automatically.
You are offered two options once you open the application one is whether you want to transfer data between two PC's connected on the same local area network or you want to prepare an image file that includes all your data that you want to keep after upgrading to a different Windows operating system.
Salient features
-
The main highlight of EaseUS Todo PCTrans is that it can also backup installed programs apart from backing up personal files.
-
Two ways of transferring data. One is data transfer between PC's connected on the same LAN and other is creating an image of files for future use.
NOTE: Data and Applications cannot be transferred using this tool from a newer OS to an older OS. You can use this in all Windows versions from XP to 10. Windows Server 2003, 2008 and 2012 are supported too.
-
You can migrate anti-virus software.
-
You can also filter your content which is to be migrated
-
It Supportes cleaning local system disks and large files.
Edition Options
You are provided with two buying options. One is the professional edition and other is the technician edition.
Both amateurs and professionals can use this tool as you are provided with a user guide and 24*7 service and live chat and a free trial of both versions.
The professional edition is for $49.95. With all the salient features available it lacks features like you can't transfer domain accounts, free tech support is medium. It is not for business use and only 2 PC's are provided with a license.
On the other hand, the Technician edition is for $399. The tech support is high. You are provided with technician license which means multiple clients can use it in a company. Technical service is provided to clients.
Conclusion
EaseUS Todo PCTrans Professional is a highly recommend OS migration or a data transfer tool.
Because of its advanced functionality and user-friendly interface, this tool can be used by amateurs as well as professionals without any issues.
You don't need to worry about your data loss as it becomes extremely easy and quick task to migrate to a new Window's OS with all your essential data safe.
A malware by its simplest definition, could be defined as a piece of code that has been specifically written to cause problems for anyone who downloads/installs it on their computer. It can be a fully developed software with malicious intents, or it could be a short program, written only to hijack/damage/disrupt a specific function on the infected computer.
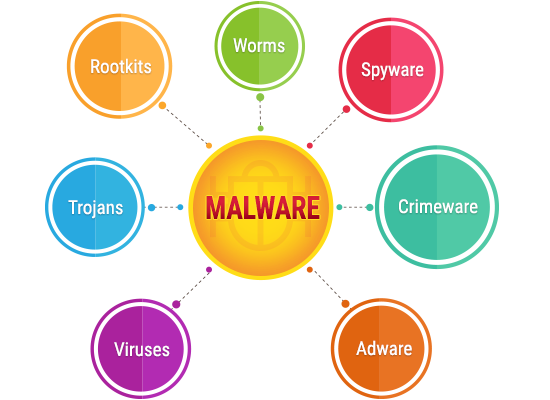
Keep in mind that malware is a very broad classificatory term which can be divided into several different types of malicious codes, based on their primary goal, medium of infection and mode of operation. A virus is just one of those multiple different types of malware, and while it can very well be the most dangerous thing that your computer can catch, it isn't the only type of malware that you should be worried about.

Understand the Threats Which a Virus Can Bring to Your Computer
Before we discuss the various other potential threats, it is imperative that we first discuss the oldest and most common type of malware first, aka a virus. Depending on the kind of infection you have, its effects may vary, and the following would be the usual suspects.
• Boot Sector Virus - The boot sector virus Infiltrates, infects and corrupts the MBR via USB/optical drives
• Resident Virus - Resides in hardware memory and cannot be removed by removing the infected file alone; also spread via physical storage/drives
• Cavity Virus - An extremely hard to notice virus that installs itself in between the gaps in the data of an installed program
• Direct Action Virus - Similar to a resident virus, it installs itself onto the hardware memory, but cannot survive without the core file
• Overwrite Virus - The primary email virus just overwrites or deletes every file it infects, making the user lose valuable information
• Multipartite Virus - Simultaneously infects and corrupts the MBR, as well as the executables
• Polymorphic Virus - The signature will be different with every single replication of a polymorphic virus, making it difficult to identify and eliminate a polymorphic infection
• Macro virus - Infects a MS Word file most often, and replaces the original macro command's execution, without changing the input

What Else Can Your Computer Catch?
Depending on the kind of sites you visit, the type of business you are in and how well your computer is/isn't protected online and offline, you could be looking at any one or possibly multiple of the following malware infections which are not classified as viruses, but can be just as, if not even more dangerous than the average computer virus.
• Trojan horse - Steals information and acts like a beneficial software
• Worm - Corrupts and deletes everything it comes in contact with, including the critical OS files necessary to run the specific OS
• Spyware - Tracks and spies on your online and offline activities
• Malicious adware - Adware designed to show ads that lead to malicious pages
• Ransomware - hijacks your computer and asks for a ransom to let you gain access back to your own data
• Fileless malware - A fileless malware has no file of its own but infects and uses genuine, installed program files to execute malicious commands
• Rootkits - Rootkits act as a restrictive barrier which protects a virus from both discovery and elimination
• Keyloggers - A spyware that logs and sends out information regarding all your keypresses (passwords, credit card data, bank data, etc. could be stolen easily)
• Malware bots - Takes over the infected computers and every infected computer might act as a hive mind, forming a botnet

What about Phishing and Spear Phishing?
In order to land on a phishing page, the user must make one of the two following mistakes:
1. Type in the wrong URL
2. Click on a link from a non-verified source
It should be noted that while phishing is an extremely dangerous threat to your online safety on any unprotected computer, it cannot be categorized as a malware. Phishing and spear phishing attacks do not infect a computer, but leads the user to a malicious page designed to replicate a universally/personally trusted website. The objective of all phishing attempts is to steal sensitive and valuable data from the user, which may include but is not limited to:
- Usernames and passwords used on the very site that the phishing page is replicating
- Other usernames and passwords used on related/unrelated websites
- Contact details and address information
- Financial information such as asset records
- One Time Passwords (OTP)
- Bank account numbers
- Other bank details
- Debit/credit card numbers
- CVC numbers
- Social security numbers
To avoid such a mishap, always check the URL for spelling mistakes or any difference in the link's structure, as compared to the genuine link, before entering sensitive information. Also, never click on an unverified link. Spear phishing uses personal information that is extremely likely to be considered as relevant by the specific individual/organization targeted. The attacker will be using personal information to make you believe in the authenticity of their email/message, all in the hope of making you click on that phishing link. Even the page where you land could have sensitive information on it, that they have likely stolen by using a malware already.

Can We Truly Protect Our Computers and Personal/Financial Information from Online Threats?
The answer is yes, we can keep our computers and our personal data protected from online and even physical media related threats because the solution is quite straightforward. Get complete web protection from one of the top antimalware developers such as Norton, McAfee or Kaspersky and keep all your devices protected against malware and phishing attempts. Thanks to massive discount coupons easily available online, this can be more affordable than you think. Without the discounts though, total antimalware protection can become a bit costly to keep up with, especially if you have multiple devices, which most of us do.
In spite of how dangerous it might be for us to use the internet today, the top antivirus and overall antimalware software providers are more than capable of handling nearly every kind of cyber threat out there, including zero-day attacks. That being said, every now and then, a malware does come around which infiltrates the defenses of even enterprise grade antimalware programs. Such instances are pretty rare though and patches are developed almost immediately after a few initial infiltrations, which stops the spread quickly.
There is a popular myth that Macs are not susceptible to malware, so anyone who believes that is advised to check for information regarding the ThiefQuest ransomware to know better. Keep all your installed programs updated, including your antivirus software to stay protected at all times, irrespective of the OS. Don't forget to enable browser protection as well, which should come by default with any of the top antivirus software solutions to keep you safe from infected sites and phishing pages.
Finally, just in case you are still using a pirated version of Windows, or a genuine copy of now-defunct Windows XP, buy an original key and update your PC immediately. Most of the time, pirated Operating Systems come with their own embedded malware, and even the versions that do not, cannot be updated. What all this means is that if the OS itself is pirated; nothing can save a computer running a pirated OS from becoming infected.

If you have a passion for computers and technology, then you are spoilt for choice when it comes to hobbies. There are all kinds of different hobbies which you could enjoy in your spare time, many of which you can easily do from home and whenever you have a spare moment so they can be easy to integrate even into a busy lifestyle. With so many options to choose from, it can be hard to decide, so here are a few of the best hobbies that you should consider if you are looking for a fun new activity in your life.
Animation
Animation is a great hobby to start because it can be incredibly rewarding seeing a project come to life, and the possibilities are endless (try taking inspiration from the many great animated films over the years). Additionally, this is a hobby that combines technical ability with creativity so it can develop many skills, and it is something that many computer lovers get a real kick out of.
Video Games
One of the more obvious hobbies for tech and computer lovers is video gaming. Video games can be fantastic fun and even develop a range of skills, plus there are many new and old games to play with a type for every different person. This is a hobby that you can easily enjoy by yourself, but it could also be social, whether this is inviting friends over or even playing against people online.
Online Casino

Following this, another fun hobby that you can easily play on your phone (which means that it can be done anywhere) is online casino games which can be an exhilarating and enjoyable way to spend time. Unibet classic slots are very popular and for a good reason, as they are colorful, engaging, and fun, and these are games that you can very quickly pick up and play with no real skill required.
Build Your Own PC
:format(webp)/cdn.vox-cdn.com/uploads/chorus_image/image/61432737/akrales_180824_2838_0014.0.jpg)
Perhaps the most rewarding hobby for any computer/tech lover is to build your own PC from scratch. There is no feeling quite like building your very own computer, plus this can be a great way to learn more about computers and build one which is high-performing and better than your average machine.
Coding

Coding is a great skill to learn, it is one which is seen as very valuable in today's day and age, so it could even help you with your career. For computer and tech lovers, many of them love the idea of coding as it is like a very complex puzzle, and this means that it is incredibly rewarding once you have a code that works and can allow you to do many great things.
These are just a few of the best hobbies for computer lovers, but there are many others to consider. Computing and technology play such a massive role in modern-day life, so there are always fun, rewarding, and enjoyable hobbies to enjoy, plus many of these are ones that you can easily do from the comfort of your own home.
© 2023 YouMobile Inc. All rights reserved





