Search result
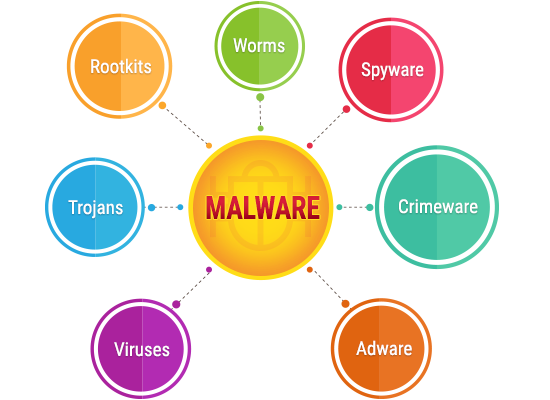
A malware by its simplest definition, could be defined as a piece of code that has been specifically written to cause problems for anyone who downloads/installs it on their computer. It can be a fully developed software with malicious intents, or it could be a short program, written only to hijack/damage/disrupt a specific function on the infected computer.
Keep in mind that malware is a very broad classificatory term which can be divided into several different types of malicious codes, based on their primary goal, medium of infection and mode of operation. A virus is just one of those multiple different types of malware, and while it can very well be the most dangerous thing that your computer can catch, it isn't the only type of malware that you should be worried about.

Understand the Threats Which a Virus Can Bring to Your Computer
Before we discuss the various other potential threats, it is imperative that we first discuss the oldest and most common type of malware first, aka a virus. Depending on the kind of infection you have, its effects may vary, and the following would be the usual suspects.
• Boot Sector Virus - The boot sector virus Infiltrates, infects and corrupts the MBR via USB/optical drives
• Resident Virus - Resides in hardware memory and cannot be removed by removing the infected file alone; also spread via physical storage/drives
• Cavity Virus - An extremely hard to notice virus that installs itself in between the gaps in the data of an installed program
• Direct Action Virus - Similar to a resident virus, it installs itself onto the hardware memory, but cannot survive without the core file
• Overwrite Virus - The primary email virus just overwrites or deletes every file it infects, making the user lose valuable information
• Multipartite Virus - Simultaneously infects and corrupts the MBR, as well as the executables
• Polymorphic Virus - The signature will be different with every single replication of a polymorphic virus, making it difficult to identify and eliminate a polymorphic infection
• Macro virus - Infects a MS Word file most often, and replaces the original macro command's execution, without changing the input

What Else Can Your Computer Catch?
Depending on the kind of sites you visit, the type of business you are in and how well your computer is/isn't protected online and offline, you could be looking at any one or possibly multiple of the following malware infections which are not classified as viruses, but can be just as, if not even more dangerous than the average computer virus.
• Trojan horse - Steals information and acts like a beneficial software
• Worm - Corrupts and deletes everything it comes in contact with, including the critical OS files necessary to run the specific OS
• Spyware - Tracks and spies on your online and offline activities
• Malicious adware - Adware designed to show ads that lead to malicious pages
• Ransomware - hijacks your computer and asks for a ransom to let you gain access back to your own data
• Fileless malware - A fileless malware has no file of its own but infects and uses genuine, installed program files to execute malicious commands
• Rootkits - Rootkits act as a restrictive barrier which protects a virus from both discovery and elimination
• Keyloggers - A spyware that logs and sends out information regarding all your keypresses (passwords, credit card data, bank data, etc. could be stolen easily)
• Malware bots - Takes over the infected computers and every infected computer might act as a hive mind, forming a botnet

What about Phishing and Spear Phishing?
In order to land on a phishing page, the user must make one of the two following mistakes:
1. Type in the wrong URL
2. Click on a link from a non-verified source
It should be noted that while phishing is an extremely dangerous threat to your online safety on any unprotected computer, it cannot be categorized as a malware. Phishing and spear phishing attacks do not infect a computer, but leads the user to a malicious page designed to replicate a universally/personally trusted website. The objective of all phishing attempts is to steal sensitive and valuable data from the user, which may include but is not limited to:
- Usernames and passwords used on the very site that the phishing page is replicating
- Other usernames and passwords used on related/unrelated websites
- Contact details and address information
- Financial information such as asset records
- One Time Passwords (OTP)
- Bank account numbers
- Other bank details
- Debit/credit card numbers
- CVC numbers
- Social security numbers
To avoid such a mishap, always check the URL for spelling mistakes or any difference in the link's structure, as compared to the genuine link, before entering sensitive information. Also, never click on an unverified link. Spear phishing uses personal information that is extremely likely to be considered as relevant by the specific individual/organization targeted. The attacker will be using personal information to make you believe in the authenticity of their email/message, all in the hope of making you click on that phishing link. Even the page where you land could have sensitive information on it, that they have likely stolen by using a malware already.

Can We Truly Protect Our Computers and Personal/Financial Information from Online Threats?
The answer is yes, we can keep our computers and our personal data protected from online and even physical media related threats because the solution is quite straightforward. Get complete web protection from one of the top antimalware developers such as Norton, McAfee or Kaspersky and keep all your devices protected against malware and phishing attempts. Thanks to massive discount coupons easily available online, this can be more affordable than you think. Without the discounts though, total antimalware protection can become a bit costly to keep up with, especially if you have multiple devices, which most of us do.
In spite of how dangerous it might be for us to use the internet today, the top antivirus and overall antimalware software providers are more than capable of handling nearly every kind of cyber threat out there, including zero-day attacks. That being said, every now and then, a malware does come around which infiltrates the defenses of even enterprise grade antimalware programs. Such instances are pretty rare though and patches are developed almost immediately after a few initial infiltrations, which stops the spread quickly.
There is a popular myth that Macs are not susceptible to malware, so anyone who believes that is advised to check for information regarding the ThiefQuest ransomware to know better. Keep all your installed programs updated, including your antivirus software to stay protected at all times, irrespective of the OS. Don't forget to enable browser protection as well, which should come by default with any of the top antivirus software solutions to keep you safe from infected sites and phishing pages.
Finally, just in case you are still using a pirated version of Windows, or a genuine copy of now-defunct Windows XP, buy an original key and update your PC immediately. Most of the time, pirated Operating Systems come with their own embedded malware, and even the versions that do not, cannot be updated. What all this means is that if the OS itself is pirated; nothing can save a computer running a pirated OS from becoming infected.

In a time when the world has invariably moved on to the rectangular brick form in varying sizes, Samsung is one of the few companies in the entire world that has not abandoned the flip phone completely yet. It's not like that the Korean company simply produces legacy devices just to keep the flip phone alive mind you; these are fully-fledged smartphones with top-of-the-line chips, Sufficient RAM, internal storage and the latest Android Operating Systems. The latest addition to this long line of flip smartphones is going to be the SM-G9298. No other name has been revealed for the handset so far, but it should be announced on August 3rd, during an exclusive media event by Samsung in Beijing, China. This is of course leaked news brought to us by @mmddj_china on Twitter. Check out the specs of the upcoming device below, as per the leaks so far.
• Two 4.2-inch displays; one on the outside and the other on the inside
• Qualcomm Snapdragon 821 SoC
• 4GB RAM
• 64GB of internal storage
• 12-megapixel rear and 5-megapixel front camera
• 2,300mAh battery with wireless charging
Check out the image above and let us know if you would buy one if you could.
Via: SamMobile
Saikat Kar (tech-enthusiast)

Artificial intelligence has been the stuff of science fiction for years, but now that it is becoming a reality, our world is changing in ways we never imagined. AI is more than a buzzword or a catchy phrase, it is an intelligent machine learning that will continue to optimize our lives and lead to unexpected outcomes. It is no surprise that technology companies have been using AI to market to their customers in new ways. AI-driven apps for web design and mobile marketing are changing everything when it comes to the mobile user experience. They, for all intents and purposes, can know the consumer wants before they want it. Everyone from e-commerce companies to airlines, hotels, and brick-and-mortar businesses are using AI to enhance their customers' experience, but how are they doing it?
AI Marketing
AI and machine learning are being used in innovate ways to come up with new marketing techniques and methods. Facial recognition software, voice assistants, and augmented reality are finding solutions to daily problems. With the vast amount of data available to companies like Amazon and Google, they are able to collect information about people and utilize AI to figure out exactly what the consumer wants, even before they actually want it.
Every mobile device from Samsung to Apple to Google contains hardware designed to handle AI. This has made the technology grow far and wide. While just in 2017 there were only three percent of phones that had AI capabilities, 35 percent of all mobile devices will have AI technology next year.
The technology is being used to market to both old and new customers by changing the way people interact with their devices and encouraging people to buy goods and services. By collecting people's data and analyzing it, technology can determine how a demographic will respond to a particular marketing strategy. This is valuable information to just about every business.
Machine learning and sophisticated algorithms can target audiences and avoid scattering their efforts on irrelevant leads. Companies who run mobile apps are boosting both sales and engagement. AI tools are being used to promote to the right people sooner and more effectively than traditional methods according to MoneyPug, a price comparison site known as a platform to find the best mobile phone plans.
AI Software
There are specific categories when it comes to AI development. First there is analytics. Then content management, ad optimization, email marketing, customer service, and social media management. Tools to analyze data are the methods being used to optimize user experience. By processing massive amounts of data, companies can predict customers' decisions based on their choices in the past.
Ad optimization tools are a feature that helps manage all ad campaign data in a single place. They provide the ability to deliver customized workflow and Machine Learning recommendations to automate and create ads. AI generates relevant ideas for new content and communications. Chatbots can greet visitors to the website and provide assistance that can be of assistance when a customer needs help.
AI Apps
The tools of artificial intelligence apps are AI-enabled apps that deliver adaptive and personalized user experiences. This software combines the power of predictive analytics with cutting-edge technologies, as well as operational and consumer data. The latest user-centric app development tools can create an unbeatable user experience with action and data-driven Omnichannel tools that are adaptive.
Cortana is one of these apps. Microsoft's personal assistant
offers features to users that can keep track of important files and documents
while setting reminders and obtaining insight into the weather, traffic, and
more. Socratic is an AI app by Google that simplifies the learning process and
empowers students. IRIS is an intelligent reporting app for leaders and
managers. All of these and more are being used by companies to optimize the
user experience on mobile devices and market to those they need to.
However you fell about AI, it is changing everything, including business. These marketing tactics are far beyond anything that we have had before, and we will need to reconcile what this means. With data being collected and used to make large companies very wealthy, our society needs to decide how much information we want to give up and what we want to keep to ourselves.

How would you react if your next iPhone came without the 3.5mm jack? The 3.5mm audio port has been the basic universal standard for all media-capable devices and even basic phones for the last several years. According to the latest rumor about the upcoming iPhone 7, Apple is removing it from their future products. What makes this rumor scarier is the fact that it supposedly came from the iPhone 7 supply chain!
We are unsure as to why Apple would even make this move as we can clearly predict issues with such a decision from the word go. Firstly, the new lightning port is incapable of supporting analog audio unlike the previous Apple 30-pin connector. Even if a regressively proprietary set of costly headphones with built-in amp and Digital-to-Analog Converter is made available, it would definitely strain the battery in addition to becoming far too complicated. Moreover, this would prevent the user from charging the phone while using headphones.
Wireless audio will possibly be a better option if Apple really goes through with this move as your new Apple headsets won't be compatible with anything else you own anymore. In our opinion, the chances of this rumor turning out to be true are pretty slim as the decision would unnecessarily complicate things for the iPhone 7 and frankly, we cannot see a viable reason as to why the company would make such a change to begin with!

Steve Jobs used to make a last second product announcement during Apple media events by uttering three words that became associated with him. "One more thing" Jobs would say, in a manner that immediately recalled Peter Falk's portrayal of television detective Columbo. Last week, it was discovered that watchmaker Swatch had trademarked the line in May, one month after the introduction of the Apple Watch.
One of the reasons that Apple's timepiece isn't called the iWatch has to do with a threat made by Swatch, which owns the iSwatch trademark. Swatch said that consumers could easily confuse the iWatch and iSwatch names, and promised to take legal action against Apple if necessary.

Today, Swatch announced that a sequel to the Touch Zero One, the Touch Zero Two, will be launched at the 2016 Olympic Games in Rio de Janeiro. The watchmaker will also offer new smartwatches later this year with support for NFC. This could allow the device to be used to make mobile payments and might be perceived as more of a challenge to the Apple Watch.

Recently, Apple launched a new advertisement campaign that offers you to trade-in your old iPhone with Apple for a discount on an upgrade to the new one. Apple consider three years as a potential life of an iPhone before it is hand over to someone else to be sold as second hand handset or stored in any drawer when a new iPhone is purchased. With the latest offer, Apple is making a new shifting trend to increase the number of upgrades to new iPhone by customers by returning the handset to Apple and trade it in for a new phone.
There are a few advantages for Apple in the offer. The user will still remain in the Apple's echo system if they upgrade their handset to another iPhone. Apple's CEO Tim Cook seems to put a great emphasis on services Apple can bring to its customers. Apple is using the emotional call back by Steve Jobs "One last thing" in the advertisement as handing back to your iPhone to Apple, it is available for refurbished and "put back into the world". If the iPhone you hand over is too old or have expected life span less than one year, it will get recycled in way that "respects the planet" and not by adding more plastic pollution to the planet.
Here is what Apple's new ad says:
You've done great things with your iPhone. But at some point, you'll be ready for something new. You can easily trade it in with Apple, so it can be refurbished and put back into the world, so someone new can do their own great things with it.
But if your device is at the very end of life, materials inside will be recovered and recycled. Either way, you can continue to do what you love, while respecting the planet.

If there's anything I find annoying on the latest Samsung smartphones, that would be the lag. In spite of always sporting the best hardware on paper, Samsung smartphones are always bogged down by its UI. While the latest UI (Samsung Experience) is indeed a more stripped down version of the infamous TouchWiz, it still lags more than it should unfortunately. However, an official update for the Galaxy S8 from Samsung has been released with the sole objective of solving all issues of lag on the Home UI.
After going through forums and premier sites, I noticed that a lot of the users who have already downloaded and installed the update are reporting that the update does indeed solve the lag problem to a great degree. As Samsung devices have the unfortunate tendency to become more and more laggy with time, we will have to wait and see how well this works after a few months have gone by. In addition to addressing lags, the update also improves the visibility of icons on a white background, as per the changelog. If you have a Galaxy S8 or S8+ and you have received the update, do let us know if you can see any noticeable difference.
Head over to our firmware section to find all the latest available updates for your Samsung smartphones and tablets.
Saikat Kar (tech-enthusiast)
© 2023 YouMobile Inc. All rights reserved





